Compartir
0
/5
(
0
)
La blockchain trajo nuevos conceptos y tecnologías que facilitan el desarrollo del mundo descentralizado y otras funciones fuera del espacio cripto.
En su origen, el hash de la blockchain es una característica central que asegura los datos, organiza las transacciones y garantiza una comunicación unificada dentro de la infraestructura DeFi.
Las funciones hash transforman los datos de entrada en salidas reguladas que son más fáciles de identificar, verificar y gestionar. Exploremos cómo funciona esta tecnología y qué lenguajes se utilizan en su desarrollo.
Puntos clave
El hash de blockchain es un método de protección y detección de datos que transforma la entrada en una salida uniforme, identificable y rastreable.
Las filtraciones y alteraciones de datos se pueden detectar fácilmente mediante hashes, ya que cualquier manipulación produce un nuevo identificador de hash.
Existen varios tipos de funciones hash que transforman los datos de manera diferente y cumplen distintos propósitos, como la verificación de transacciones, la identificación de bloques y la programación de contratos inteligentes.
¿Qué es un hash en la blockchain?
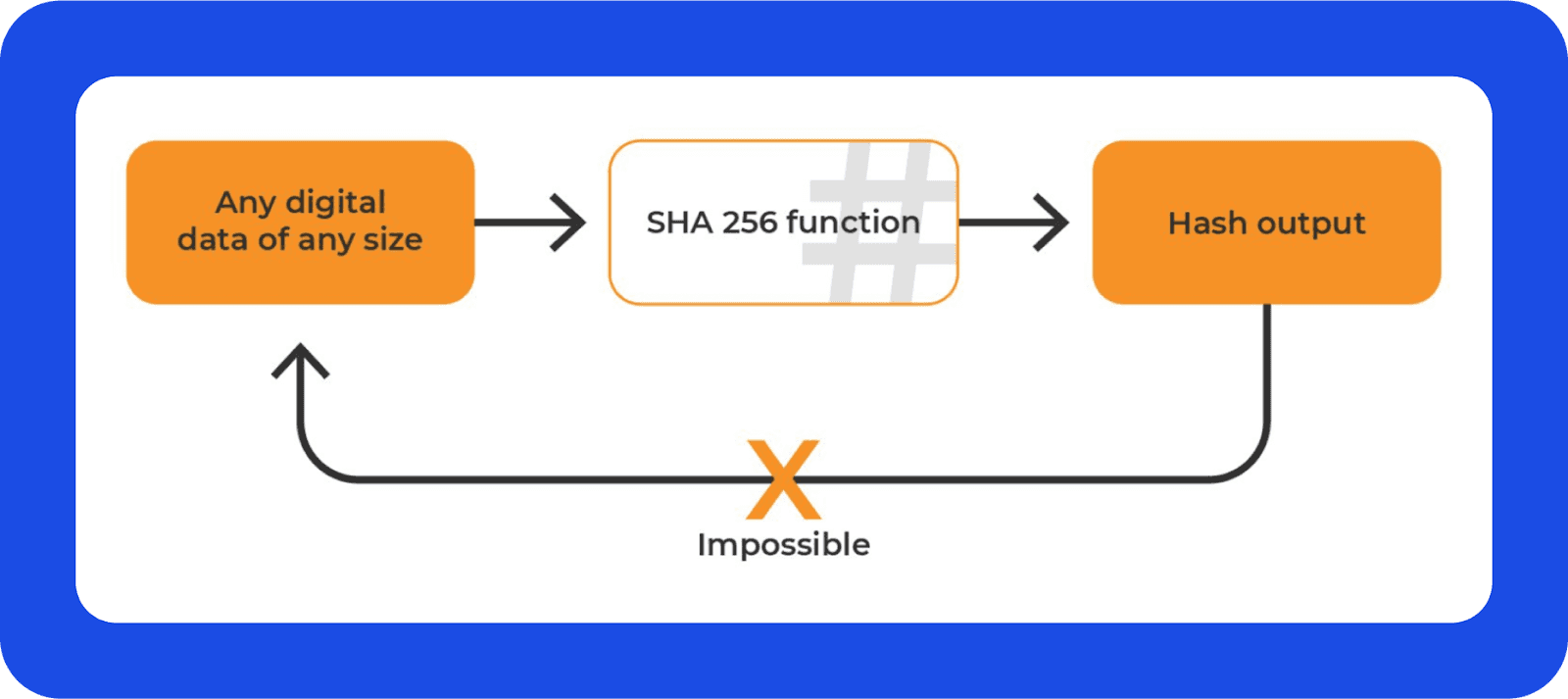
Un hash en la blockchain es una función matemática que convierte una entrada compuesta por números, texto e imágenes de tamaño variable en una cadena estandarizada de longitud fija.
Cada entrada genera un hash de transacción único en la blockchain, lo que lo convierte en un método eficiente para verificar la integridad de los datos, los cuales no pueden ser manipulados. Incluso cambios mínimos en las cadenas ingresadas pueden dar lugar a hashes diferentes, demostrando su sensibilidad.
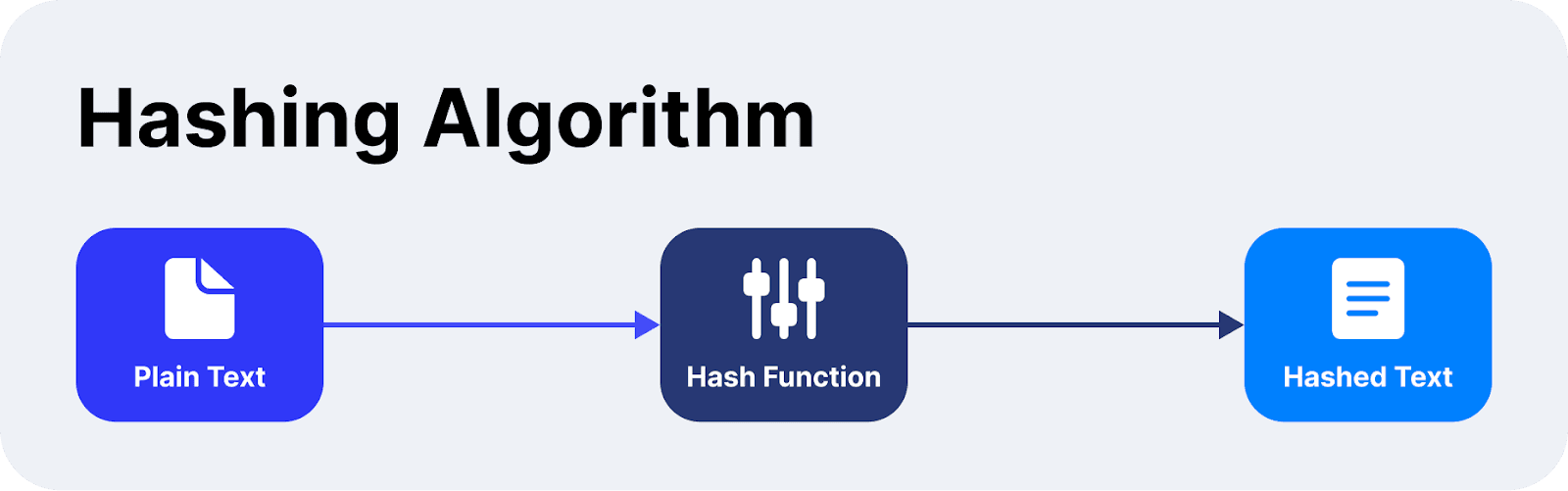
Los hashes son inmutables, lo que significa que revertir la operación para deducir la entrada original a partir del hash es imposible. Esta singularidad garantiza que los datos de la blockchain se mantengan seguros, ya que modificar cualquier información invalidaría el hash completo del bloque.
Esta propiedad lo hace indispensable para asegurar las transacciones y enlazar bloques en una blockchain.
El papel del hash en la seguridad descentralizada
Las funciones hash son fundamentales para la seguridad de la blockchain. Protegen la integridad de los datos asegurando que cualquier alteración en la información almacenada genere una nueva salida, lo que pone de manifiesto cualquier intento de manipulación.
Además, los hashes posibilitan la vinculación de bloques a través de los encabezados criptográficos, formando una cadena inmutable. Su uso en mecanismos de consenso, como Proof-of-Work (PoW), garantiza una validación de transacciones descentralizada y sin necesidad de confianza.
Además, protege los activos de los usuarios gracias a sus protocolos de seguridad en las direcciones de las carteras cripto y las firmas digitales. La dificultad computacional de generar hashes específicos protege adicionalmente la red de ataques, convirtiéndolos en componentes esenciales del marco de seguridad de la blockchain.
Evolución de las funciones hash
Las funciones hash han evolucionado enormemente, pasando de algoritmos simples como MD5 a estructuras criptográficas avanzadas como SHA-256.
En el pasado, los algoritmos se empleaban para la integridad básica de los datos y su identificación, pero resultaban insuficientes para los requisitos de seguridad modernos debido a vulnerabilidades como las colisiones —cuando dos entradas distintas generan la misma salida hash.
Los avances en criptografía han introducido protocolos más robustos con una mejor resistencia a los ataques y a los intentos de manipulación, posibilitando aplicaciones seguras en la blockchain, firmas digitales y sistemas de autenticación.
Hoy en día, los sistemas blockchain emplean algoritmos de última generación como Keccak-256 y Blake2b para asegurar la seguridad y el rendimiento de los datos. Esta evolución está en consonancia con la creciente adopción de tecnologías Web 3.0 y la demanda creciente de soluciones criptográficas robustas.
¿Cómo funciona el hash en la blockchain?
La función hash convierte los datos de entrada en una cadena de longitud fija, creando una huella digital única. La entrada se procesa a través de un protocolo de paso de mensajes que genera una salida.
Cada algoritmo hash establece protocolos de encriptación, sistemas de seguridad, la categorización de datos y el estilo de comunicación. A cada entrada se le asigna un identificador hash único, que no puede ser cambiado ni modificado, independientemente de las alteraciones que puedan ocurrir en los datos originales.
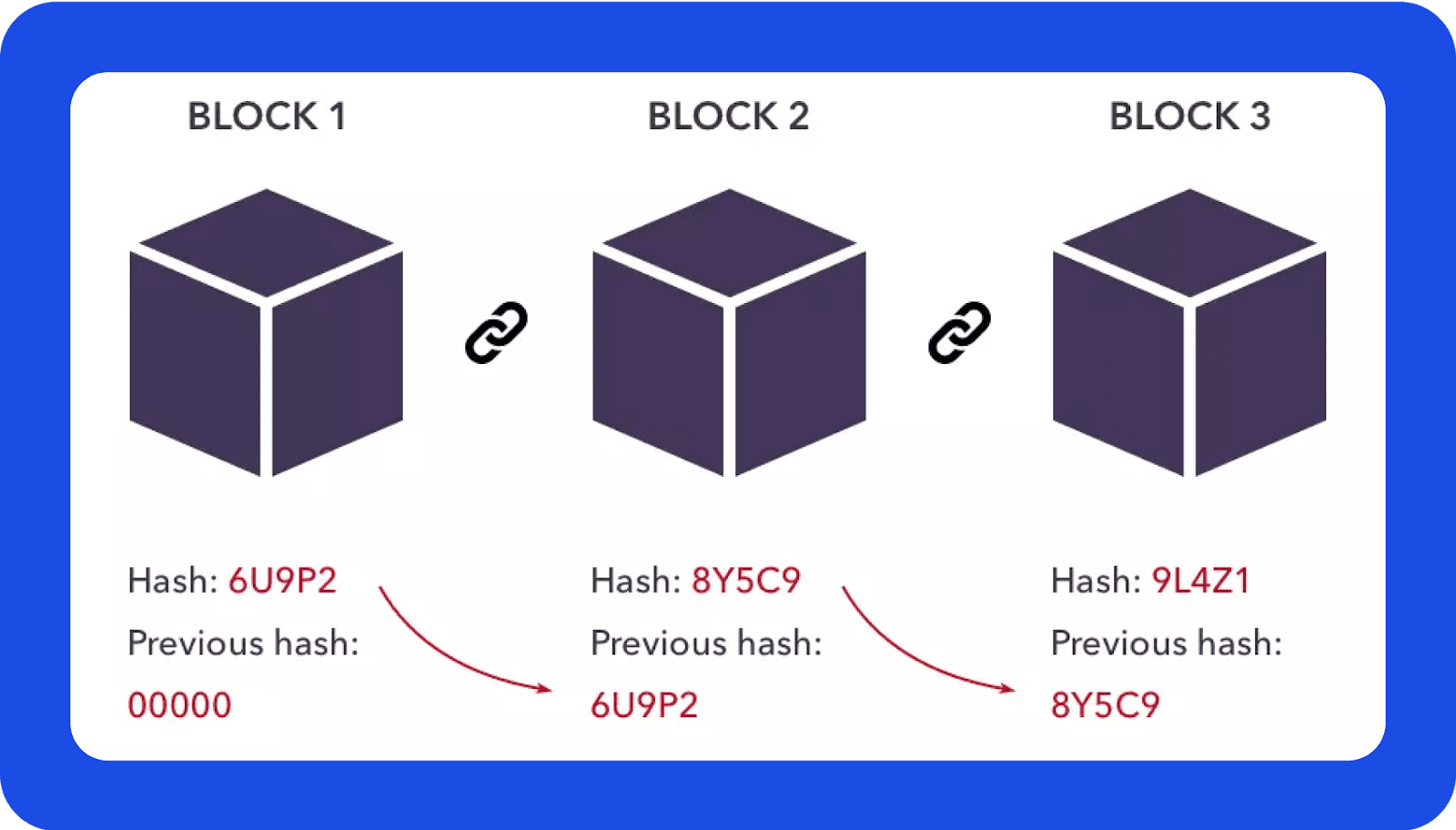
Los hashes cumplen varios roles en la blockchain:
Cuando los datos de una transacción se convierten en hash, cualquier alteración en la transacción modifica el hash, haciendo que la manipulación sea inmediatamente detectable.
Cada bloque contiene su propio hash y el del bloque anterior, formando una cadena inquebrantable. Modificar los datos de un bloque implicaría cambiar todos los bloques siguientes, lo cual es casi imposible sin recursos computacionales considerables.
El hash es fundamental en las blockchains basadas en el proof-of-work, pues los mineros resuelven complejos acertijos al encontrar un hash que cumpla con criterios específicos. Este proceso valida las transacciones y protege la red.
Los hashes se emplean para generar direcciones de cartera únicas y asegurar la privacidad y seguridad de los usuarios de la blockchain.
La irreversibilidad y sensibilidad de los hashes criptográficos los hacen indispensables para la estructura descentralizada y sin confianza de la blockchain.
Aplicaciones clave y casos de uso
Las funciones hash son la base de las aplicaciones blockchain, asegurando la seguridad, transparencia e integridad de los datos.
Sus aplicaciones se extienden más allá de la blockchain, abarcando industrias que requieren verificación de datos, autenticación y resistencia a manipulaciones. Revisemos las aplicaciones clave dentro de los sistemas DeFi y cómo los hashes contribuyen a su funcionamiento.
Verificación de transacciones
Los hashes aseguran la integridad de las transacciones al generar identificadores únicos para cada operación. Al realizar el hash de los detalles de una transacción, cualquier modificación altera el hash, permitiendo detectar manipulaciones.
Los nodos de la blockchain utilizan estos hashes para verificar las transacciones antes de incorporarlas al libro mayor público, garantizando la precisión, rastreabilidad y confiabilidad de todo el sistema blockchain.
Consenso de Proof-of-Work (PoW)
Utilizado en las blockchains de Bitcoin, Litecoin y Monero.
El Proof-of-Work (PoW) es un mecanismo de consenso utilizado en las redes blockchain, que requiere que los participantes (mineros) resuelvan complejos acertijos criptográficos. Estos desafíos implican generar un hash que cumpla parámetros predeterminados. Este proceso implica generar y analizar millones de hashes por segundo, requiriendo un esfuerzo computacional considerable.
El PoW asegura la validación descentralizada de las transacciones y protege la blockchain al hacer que la modificación de datos sea computacionalmente impracticable.
Identificación de bloques
Los hashes se asignan como identificadores únicos, permitiendo ser localizados de manera eficaz en los bloques de la blockchain. Cada bloque contiene su propio hash y se vincula con el bloque anterior.
Esta conexión asegura la inmutabilidad, puesto que alterar los datos de un bloque implicaría recalcular los hashes de todos los bloques siguientes, lo cual es casi imposible sin recursos computacionales considerables.
Contratos inteligentes
Los hashes en los contratos inteligentes verifican la integridad de los datos y activan acciones basadas en condiciones predefinidas. Por ejemplo, pueden asegurar que un valor de entrada coincida con los parámetros esperados para ejecutar automáticamente un contrato o realizar una función específica.
Esta capacidad posibilita interacciones seguras, automatizadas y sin intermediarios en las plataformas blockchain.
Carteras criptográficas
Las carteras criptográficas se apoyan en protocolos de hashing de la blockchain para generar detalles de almacenamiento únicos. Las claves públicas se convierten en hash para crear direcciones más cortas y fáciles de gestionar.
Este proceso mejora la seguridad y la privacidad al ocultar los datos originales de la clave pública, reduciendo los ciberataques y garantizando el anonimato del usuario.
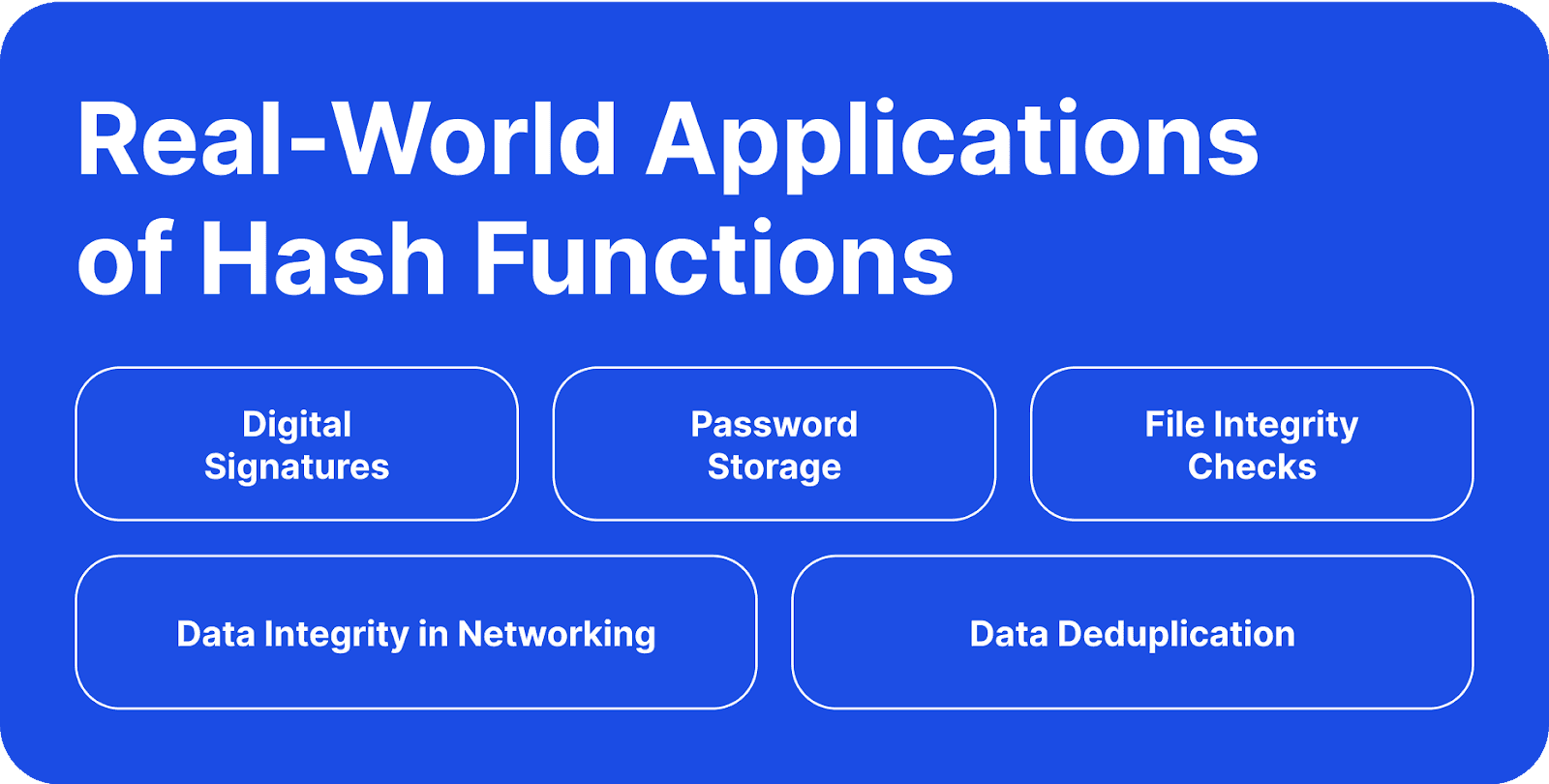
Aplicaciones fuera de la blockchain
Más allá de la blockchain, esta tecnología puede utilizarse en diversas industrias.
En ciberseguridad, se utilizan para verificar la integridad de los archivos descargados comparando los valores hash.
En la informática forense, los hashes autentican la evidencia al asegurar la integridad de los datos, especialmente en información clasificada.
Los sistemas de protección de contraseñas aplican funciones hash para almacenar las contraseñas, añadiendo una capa extra de seguridad.
Los protocolos de red, como Ethernet, utilizan el hashing para la detección de errores durante la transmisión de datos.
En el almacenamiento y compartición en la nube, se emplean hashes para localizar y recuperar archivos de manera eficiente.
El software antivirus utiliza funciones hash para identificar las firmas de malware.
Algoritmos hash en DeFi
El hashing en la blockchain funciona mediante diferentes funciones y algoritmos, cada uno con sus propias tareas y propósitos en seguridad, encriptación de datos, protección de direcciones de billeteras, y más. Algunas de estas funciones se extienden más allá de la estructura descentralizada hacia aplicaciones en la vida real.
Revisemos los algoritmos más populares.
SHA-256
El Secure Hash Algorithm (SHA-256) es una de las funciones hash más seguras y un protocolo ampliamente utilizado en Bitcoin y otras blockchains líderes, gracias a su resistencia a la infiltración y alteración de datos.
Genera un valor hash estandarizado de 256 bits, que se utiliza para crear las claves públicas y privadas en carteras y transacciones cripto. Es resistente a vulnerabilidades y colisiones, lo que lo convierte en un sistema confiable para libros mayores públicos y transacciones con criptomonedas.
Keccak-256
El protocolo Keccak-256 es la base del hashing en Ethereum, y forma parte de la familia SHA-3. Ofrece fuertes propiedades criptográficas y flexibilidad, lo que lo hace adecuado para contratos inteligentes y aplicaciones descentralizadas. Su arquitectura única incrementa la resistencia a los ataques.
Scrypt
El sistema Scrypt se utiliza en Litecoin como un algoritmo hash intensivo en memoria, que añade resistencia a los ataques de fuerza bruta (un método de romper contraseñas mediante prueba y error).
Su alto costo computacional garantiza la validación de transacciones, haciéndolo una opción confiable para criptomonedas alternativas.
X11
X11 combina 11 funciones hash criptográficas diferentes para mejorar la seguridad y la eficiencia energética. Este sistema se utiliza en la altcoin Dash, ofreciendo una mejor descentralización y resistencia que los sistemas convencionales de Circuitos Integrados Específicos para Aplicaciones (ASIC), para un ecosistema de minería más equilibrado.
Blake2b
Blake2b es un algoritmo hash rápido y seguro utilizado en proyectos blockchain como Zilliqa. Se emplea en sistemas que requieren firmas digitales, tales como almacenamiento en la nube, protocolos de comunicación, software de detección de fraudes y sistemas de control.
Su eficiencia y fortaleza criptográfica lo hacen una alternativa adecuada a algoritmos más antiguos como SHA-256, ofreciendo un mejor rendimiento en aplicaciones modernas.
CryptoNight
CryptoNight se utiliza en Monero, una red descentralizada enfocada en la privacidad y diseñada para la minería amigable con la CPU. Favorece la descentralización y el anonimato al preferir hardware de consumo sobre equipos de minería especializados.
Ethash
Ethash es fundamental en el algoritmo Proof-of-Work (PoW) de Ethereum, el cual es intensivo en memoria y resistente a los ASIC. Utiliza “Grafos Acíclicos Dirigidos” para garantizar una minería descentralizada y una validación segura de transacciones, priorizando la equidad y la seguridad de la red.
RIPEMD-160
RIPEMD-160 se utiliza en Bitcoin para crear direcciones de billetera asignando identificadores únicos a las claves públicas. Tiene un tamaño de almacenamiento reducido y capacidad de resistencia a colisiones, lo que lo convierte en un protocolo eficiente para asegurar las identidades de los usuarios en redes blockchain.
[aa quote-global]
Dato Rápido
En 2017, Google enfrentó una gran colisión de datos utilizando un algoritmo de hash obsoleto, SHA-1, lo que expuso vulnerabilidades en los certificados HTTPS y las firmas digitales, provocando un cambio hacia algoritmos más robustos como SHA-256.
[/aa]
Hashing vs Encriptación
El hashing y la encriptación son dos técnicas criptográficas que funcionan de manera diferente y cumplen propósitos similares. Mientras que el hashing impide la manipulación, la encriptación protege los datos evitando accesos no autorizados.
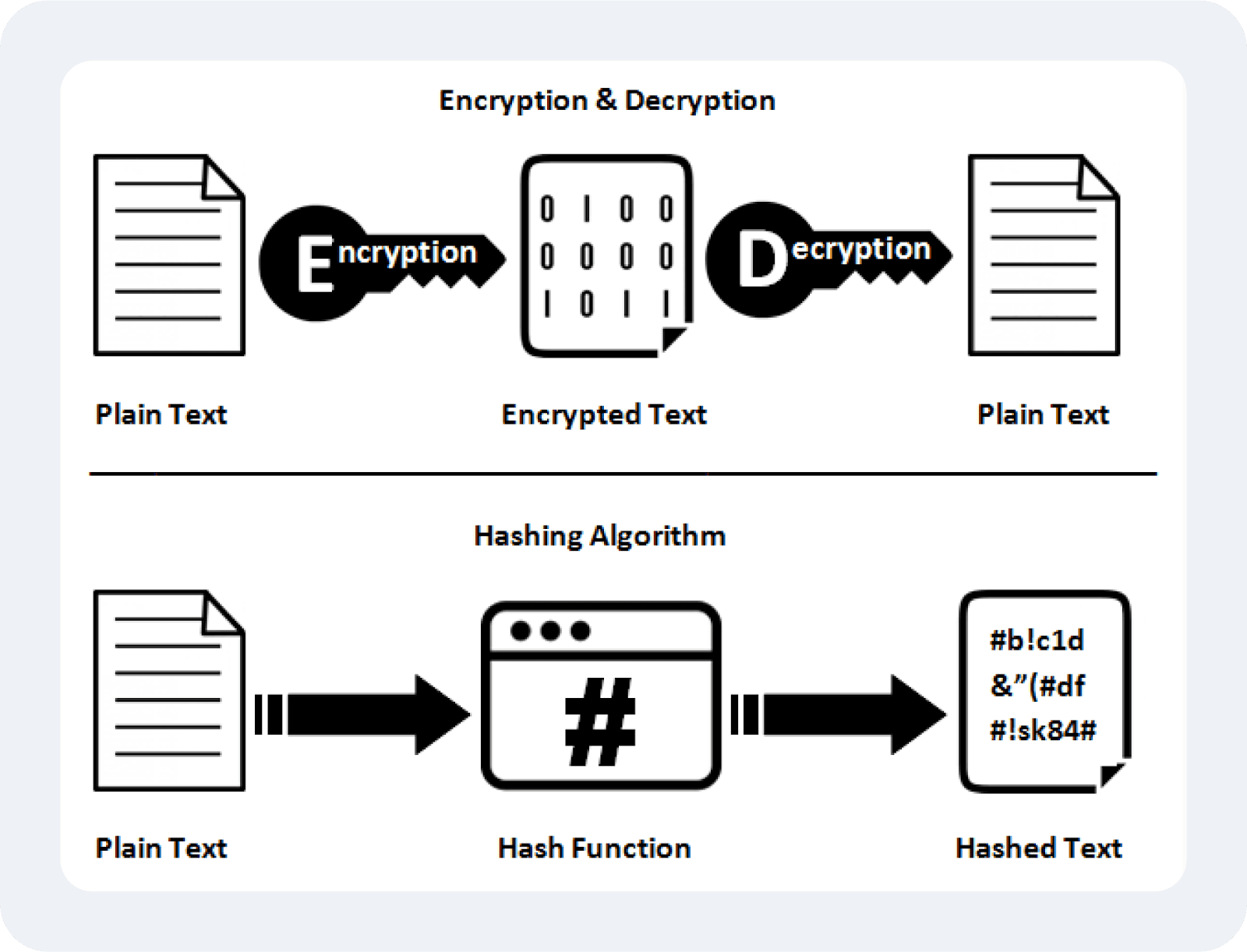
Hashing es un proceso unidireccional que crea una cadena de representaciones de datos de longitud fija, que no pueden revertirse a la entrada original ni alterarse con nueva información. Estas características garantizan la integridad de los datos y la resistencia a manipulaciones. El hashing es central para la seguridad de la blockchain, la verificación de transacciones, el enlace de bloques y las firmas digitales.
Encriptación es un proceso bidireccional que transforma los datos en texto cifrado, el cual solo puede ser descifrado utilizando una clave única. Este sistema garantiza que solo las entidades autorizadas puedan acceder a los datos encriptados. La encriptación se utiliza ampliamente para proteger información confidencial, comunicaciones privadas y la protección de archivos.
Ambas técnicas se complementan en las prácticas blockchain de la siguiente manera —la encriptación protege la información sensible mediante claves privadas, mientras que el hashing asegura la integridad de los datos almacenados en la blockchain.
El hashing en los mecanismos de consenso de la blockchain
El hashing es fundamental para los mecanismos de consenso de la blockchain, ya que permite operaciones de bloque seguras y una validación eficiente de transacciones. Estos mecanismos aseguran el acuerdo entre los nodos de la red sin necesidad de una autoridad central. A continuación, se muestra cómo el hashing respalda diversos protocolos de consenso.
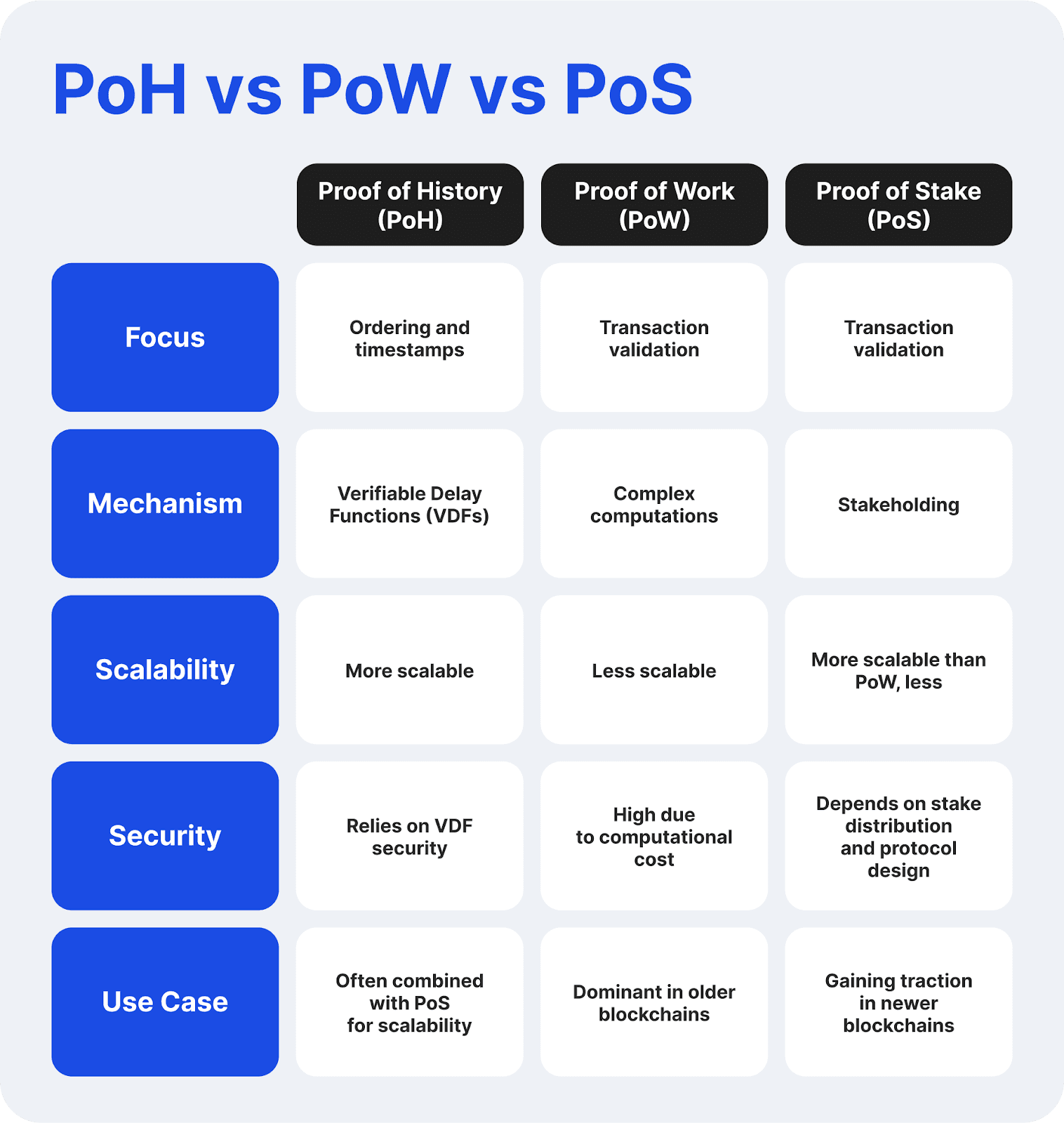
Prueba de trabajo
Utilizado en las blockchains de Bitcoin, Litecoin y Monero.
La Prueba de trabajo (PoW) es un mecanismo de consenso utilizado en las redes blockchain, que requiere que los participantes (mineros) resuelvan complejos acertijos criptográficos. Estos desafíos implican generar un hash que cumpla con criterios de dificultad específicos para validar transacciones y asegurar la red.
Este proceso, conocido como minería, requiere un esfuerzo computacional significativo, lo que hace que la manipulación sea inviable. La blockchain de Bitcoin utiliza protocolos de prueba de trabajo, como SHA-256, para enlazar bloques y mantener la inmutabilidad de la red.
La dependencia del PoW en el hashing asegura la confianza descentralizada y previene el double-spending, convirtiéndolo en uno de los mecanismos de consenso más seguros. Sin embargo, tiene un alto costo energético.
Prueba de participación
Utilizado en las blockchains de Ethereum, Solana y Cardano.
La Prueba de participación (PoS) es un sistema de consenso en el que se selecciona a los nodos para confirmar transacciones en función de la cantidad de criptomoneda que tienen en juego.
Utiliza el hashing para determinar el validador de un nuevo bloque en función de la participación del usuario en la red. De este modo, cuanto mayor sea la inversión del nodo, mayores serán las posibilidades de crear un bloque y obtener ganancias, reduciendo la necesidad de una minería intensiva en energía.
El hashing asegura la integridad de las transacciones y las propuestas de bloques, manteniendo la seguridad de la red y actuando de buena fe. Algoritmos de PoS como Casper utilizan el hashing para verificar la elegibilidad de los validadores y prevenir actores maliciosos.
Al basarse en incentivos económicos en lugar de poder computacional, el PoS logra eficiencia energética a la vez que resalta la integridad de los datos y la confianza.
Proof of History
Utilizado en la blockchain de Solana en combinación con PoS
Proof of History (PoH) es un mecanismo de sellado temporal que utiliza pruebas criptográficas para verificar secuencias de eventos, garantizando la integridad de los datos y una validación de transacciones más rápida.
Se utiliza principalmente en Solana, que sella temporalmente las transacciones para establecer un orden de eventos rastreable y verificable. El PoH crea una línea de tiempo de las entradas de datos, asegurando la consistencia cronológica sin requerir un consenso tradicional.
Emplea una función hash avanzada, en la que la salida de un hash se convierte en la entrada del siguiente. Este sellado temporal criptográfico permite un procesamiento rápido de transacciones y reduce la carga computacional asociada a los mecanismos de consenso.
El uso innovador del hashing en el PoH mejora la escalabilidad y soporta aplicaciones blockchain de alto rendimiento, convirtiéndolo en una adición única al panorama de los mecanismos de consenso.
Ventajas y desventajas
El hashing es una tecnología revolucionaria que hace que los datos, las transacciones, la comunicación y los procesos sean más seguros, especialmente en entornos descentralizados, que carecen de control centralizado. Sin embargo, a pesar de la gran cantidad de beneficios, existen algunas desventajas que merecen ser destacadas. Revisémoslas.
Ventajas
Autenticidad de los datos: El hashing en blockchain garantiza la integridad de la información al generar salidas únicas de longitud fija a partir de las entradas.
Detectabilidad: Incluso un cambio mínimo en la entrada produce un hash completamente diferente, lo que lo hace altamente fiable para rastrear y validar la información.
Seguridad en las transacciones: El hashing es fundamental para verificar operaciones, proteger las carteras y enlazar bloques en una blockchain.
Eficiencia computacional: Las funciones hash son eficientes en términos computacionales, lo que permite un procesamiento rápido de datos y la verificación de transacciones, apoyando la escalabilidad de las redes blockchain.
Protocolos sin confianza: El hashing sustenta la seguridad, transparencia y descentralización en blockchain, formando la base de la confianza en los sistemas de contabilidad distribuida.
Desventajas
Alto consumo energético: El esfuerzo computacional requerido para el hashing en PoW conduce a un desperdicio significativo de energía, generando preocupaciones ambientales, especialmente en grandes instalaciones de minería de BTC.
Amenazas de la computación cuántica: Las funciones hash enfrentan potenciales vulnerabilidades a medida que avanza la computación cuántica, lo que podría comprometer la resistencia a colisiones y exponer la blockchain a riesgos.
Necesidad de algoritmos resistentes a la cuántica: Los sistemas criptográficos requieren funciones hash resistentes a la computación cuántica para combatir las colisiones de datos, lo que hace que estos protocolos sean más complejos y costosos.
Notas finales
Las funciones hash son la columna vertebral de la tecnología blockchain, potenciando sus características de seguridad, transparencia e inmutabilidad. Impulsan la verificación de transacciones, la identificación de bloques y los mecanismos de consenso en sistemas descentralizados.
Aunque existen desafíos como el consumo de energía y las potenciales amenazas cuánticas, la evolución de los algoritmos hash continúa fortaleciendo la seguridad y la integridad de los datos en la blockchain. Las prácticas de hashing se han extendido más allá del mundo DeFi, abarcando la ciberseguridad, la informática forense y la computación en la nube.
Preguntas frecuentes
¿Qué es un hash en la blockchain?
Un hash en la blockchain es una salida única de longitud fija asignada a los datos de entrada mediante un algoritmo matemático. Se utiliza para garantizar la integridad de los datos y prevenir manipulaciones.
¿Cómo ayuda un hash a asegurar la tecnología blockchain?
Las funciones hash aseguran la blockchain al garantizar la coherencia de los datos, enlazar bloques de forma inmutable y verificar las transacciones. Cualquier alteración en los datos modifica el hash en su totalidad, haciendo que las modificaciones sean fácilmente detectables.
¿Cuál es un ejemplo de hash en la blockchain?
Un ejemplo es el algoritmo SHA-256 de Bitcoin, que convierte los datos de entrada en un hash de 256 bits utilizado para validar y asegurar los bloques, como por ejemplo el ID: 3E23E8160039594A33894F6564E1B1348BB6A40DAEDDA92C6A7573F0B9A26E4A
¿Cuál es la diferencia entre hashing y encriptación?
El hashing genera salidas irreversibles de longitud fija para la seguridad de los datos, mientras que la encriptación transforma la información en un formato reversible para proteger la confidencialidad utilizando una clave única.
Lee también