Share
0
/5
(
0
)
Guaranteeing safety and stability is central to the modern business environment, especially in the financial field, where transactions are at the highest risk. Customer Identification Programs (CIPs) play a pivotal role in this regard, serving as a crucial component of Know Your Customer (KYC) compliance for financial institutions. But what exactly is a CIP, and why is it essential?
Key Takeaways
CIPs are indispensable for financial institutions to verify the identities of their customers and comply with regulatory requirements.
CIPs encompass essential components such as identification and verification processes, recordkeeping, comparison with government lists, risk assessment and continuous monitoring.
Financial institutions must balance rigorous identity verification with delivering a seamless customer experience to enhance satisfaction and trust.
Decoding the Customer Identification Program CIP
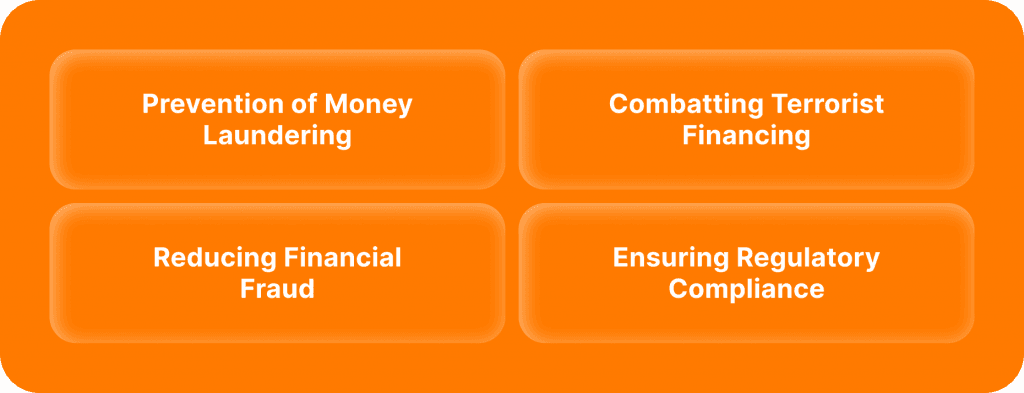
A Customer Identification Program (CIP) is a set of measures designed to verify customers' identity. It is a mandatory due diligence practice that financial organisations must conduct to fulfil their KYC obligations. Included in regulatory policies such as the USA Patriot Act and the Bank Secrecy Act, CIPs aim to detect and prevent illicit activities such as fraud, stages of money laundering, and terrorist financing.
Here are the primary objectives of customer identification program requirements:
Compliance with Legal and Regulatory Requirements
Financial institutions must adhere to laws and regulations governing customer identification to mitigate the risk of financial crime and maintain regulatory compliance.
Risk Management
By accurately verifying the identities of customers, financial institutions can assess and mitigate the risk of being involved in illicit financial activities, such as money laundering and terrorist financing.
Protecting the Integrity of the Financial System
CIPs play a crucial role in safeguarding the integrity of the financial system by preventing the misuse of financial services for illegal purposes and preserving public trust in the banking system.
Enhancing Security
Effective customer identification helps to protect both the financial institution and its customers from fraud, identity theft, and other forms of financial crime.
Overall, Customer Identification Programs are essential components of a robust anti-money laundering and counter-terrorism financing framework, helping to ensure the safety and soundness of the financial system.
The CIP rule applies to a wide range of entities, including banks, credit unions, broker-dealers, insurance companies, fintech firms, and even foreign financial institutions maintaining correspondent accounts within the United States. Compliance with CIP regulations is essential for mitigating risks and maintaining the integrity of financial transactions.
Elements of Customer Identification Program
At its core, a customer identification program elements encompass several key requirements that financial institutions must adhere to:
Customer Due Diligence (CDD)
CDD is a critical component of a Customer Identification Program. It involves the collection and verification of information about customers to assess their identity, the nature of business or activities, and associated risks. CDD typically includes the following elements:
Identity verification – Financial institutions must verify the identity of anyone applying to open an account, collecting identity proofing information such as name, address, date of birth, government-issued identification number and proof of income documents.
Beneficial ownership identification – For entities such as corporations, partnerships, or trusts, financial institutions must identify and verify the beneficial owners who ultimately own or control the entity.
Understanding the nature of the business relationship – Financial institutions need to understand the purpose and intended nature of the business relationship with the customer to assess the associated risks properly.
Comparison with Government Lists – Customer information must be verified using documentary and database verification methods, including checks against government lists to identify individuals or entities subject to sanctions or legal restrictions.
Customer Risk Profiling
Customer Risk Profiling involves assessing the risk level associated with each customer based on various factors, including their identity, nature of business or activities, geographic location, transaction history, and other relevant criteria.
The objective is to categorise customers into different risk categories (e.g., low risk, medium risk, high risk) to determine the appropriate level of due diligence and monitoring required. Key steps in customer risk profiling include:
Risk assessment – Financial institutions evaluate the inherent risks associated with different types of customers and the products or services they use.
Risk scoring – Customers are assigned risk scores based on factors such as their industry, geographic location, transaction volume, and any previous suspicious activity.
Risk classification – Customers are categorised into risk tiers based on their risk scores, with appropriate risk management measures applied to each category.
Ongoing Monitoring
Ongoing monitoring of customer behaviour helps identify any changes or red flags indicating potential fraudulent activities. Key aspects of ongoing tracking include:
Transaction monitoring – Financial institutions use automated systems and manual reviews to monitor customer transactions in real-time or near real-time, flagging any unusual or suspicious activity for further investigation.
Suspicious activity reporting – If suspicious activity is identified during ongoing monitoring, financial institutions are required to file Suspicious Activity Reports (SARs) with the appropriate regulatory authorities.
Periodic reviews – In addition to real-time monitoring, financial institutions conduct periodic reviews of customer accounts and transactions to identify any patterns or trends indicative of illicit activity.
Overall, the components of a Customer Identification Program work together to ensure that financial institutions can effectively identify and manage the risks associated with their customers while complying with legal and regulatory requirements.
[aa quote-global]
Fast Fact
The CIP Rule requires a bank to implement a program that includes risk-based verification procedures that enable the bank to form a reasonable belief that it knows the true identity of its customers.
[/aa]
Implementation of Customer Identification Programs
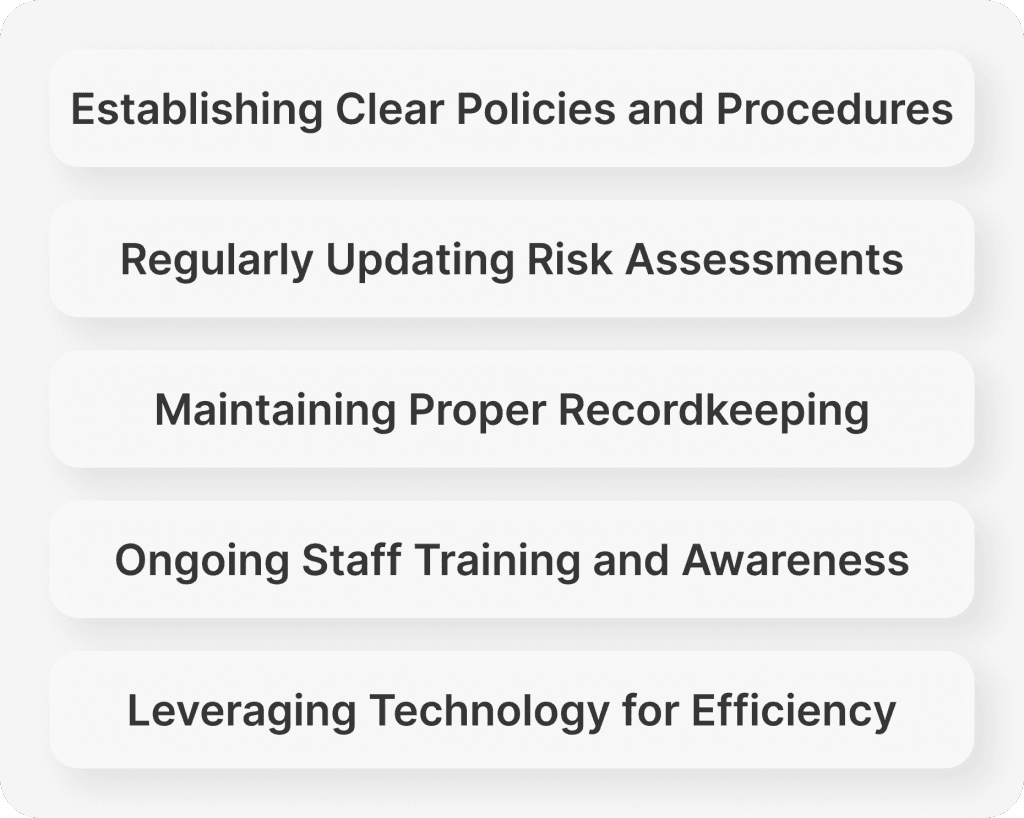
Implementing a Customer Identification Program involves several key procedures to ensure effective compliance with legal and regulatory requirements:
Policy Development
Financial institutions must develop written policies and procedures outlining the requirements and processes for customer identification and due diligence.
Customer Onboarding
Clear procedures should be established for verifying the identity of new customers, including the collection and validation of required documentation.
Risk Assessment
Financial institutions should conduct risk assessments to categorise customers into different risk levels and determine the appropriate level of due diligence required for each category.
Recordkeeping
Adequate systems and processes should be implemented to maintain accurate records of customer identification information, transaction records, and any suspicious activity reports.
Review and Update
CIP procedures should be periodically reviewed and updated to reflect changes in regulatory requirements, industry best practices, and emerging risks.
Integration with existing processes and systems is essential for seamless implementation and operation of a CIP. This may involve:
Integration with CRM Systems
CIP procedures should be integrated with existing CRM systems to streamline customer onboarding and data management processes.
Compliance Software
Financial institutions may utilise compliance software solutions to automate customer screening, risk assessment, and transaction monitoring processes.
IT Infrastructure
CIP procedures should be integrated with the institution's IT infrastructure to ensure secure storage and access to customer identification data and transaction records.
Training and Support
Staff should receive training and support on how to use integrated systems and follow them effectively.
KYC vs CIP
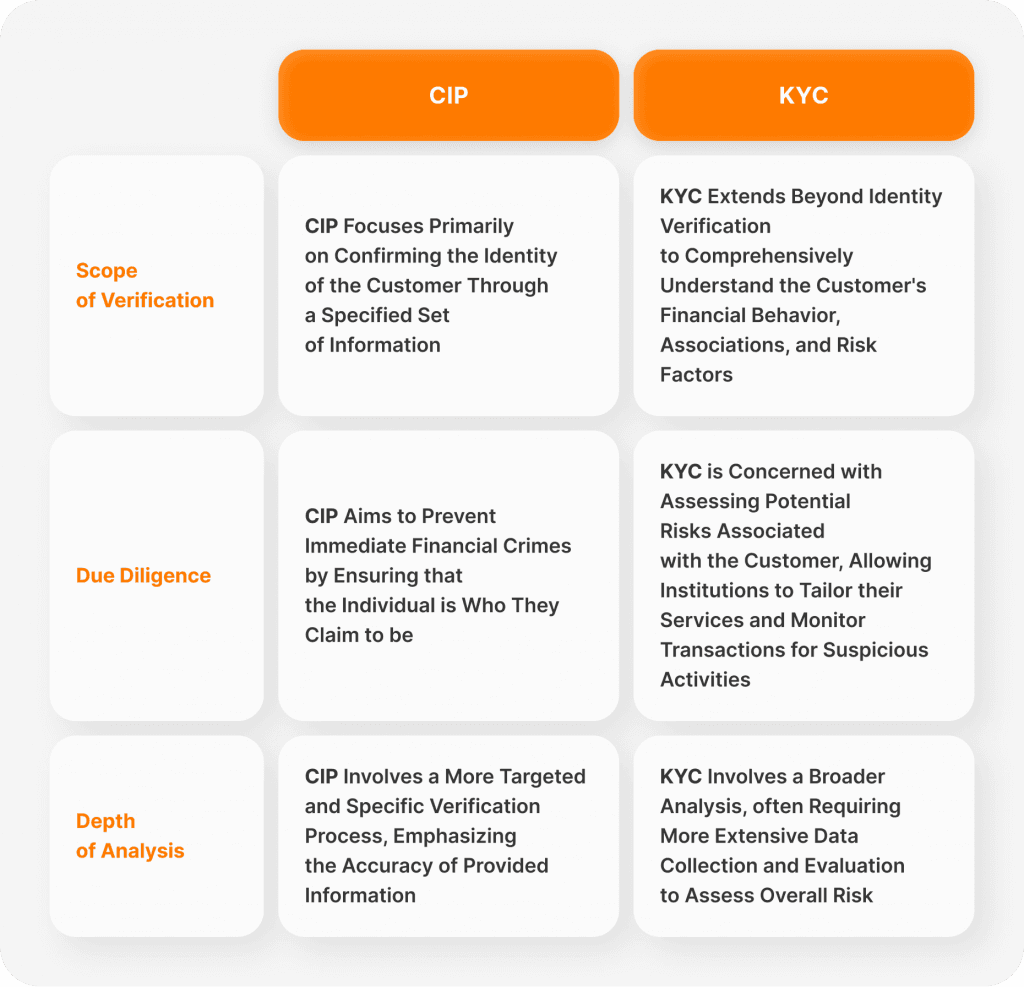
While CIP focuses on verifying customer information, KYC goes beyond identification to encompass a broader understanding of a customer's profile, financial history, and risk level. KYC involves enhanced due diligence processes to assess potential risks associated with the customer and ensure compliance with regulatory requirements.
KYC (Know Your Customer)
KYC refers to the process of verifying the identity of customers and assessing their potential risks of illegal intentions such as money laundering or terrorist financing.
It involves collecting and verifying various types of customer information, such as identity documents, addresses, occupation, source of funds, and purpose of the account or transaction.
The purpose of KYC is to ensure that financial institutions have adequate information about their customers to understand their financial dealings, assess their risk profile, and detect any suspicious activities.
KYC is an ongoing process, meaning that institutions periodically review and update customer information to ensure its accuracy and relevance.
CIP (Customer Identification Program)
CIP is a subset of KYC and specifically refers to the process of verifying the identity of customers when they open a new account.
It requires financial institutions to collect specific information from customers, such as name, date of birth, address, and identification number.
The purpose of CIP is to establish the identity of customers at the time of account opening to prevent identity theft, fraud, and other illegal activities.
CIP is a one-time process that occurs at the beginning of the customer relationship, although institutions may update customer information as needed during the course of the relationship.
In summary, while KYC is a broader process that involves continuously verifying and monitoring customer identities and activities, CIP is a specific requirement within KYC that focuses on verifying customer identities at the time of account opening.
Conclusion
While CIPs are critical for preventing fraudulent activities, they can also impact the customer experience. Financial institutions must strike a balance between rigorous identity verification and seamless onboarding processes to enhance customer satisfaction while ensuring compliance with regulatory requirements.
In conclusion, CIPs are indispensable for financial institutions in combating financial crimes and maintaining regulatory compliance. By adhering to CIP requirements and implementing robust verification processes, institutions can safeguard against fraud, money laundering, and other illicit activities, thereby fostering trust and security in the financial ecosystem.
FAQ
What are the main requirements of the customer identification program (CIP) rule?
There are minimum requirements that all CIPs must include in the procedures for obtaining and verifying customer-identifying information, such as name, date of birth, and address.
What is first-party fraud?
First-party fraud is when an individual or an organisation purposely misrepresents their identity or provides incorrect information to gain an unfair or unlawful advantage.
How many CIP standards are there?
The NERC CIP consists of 11 standards that protect against cybersecurity attacks.
Read also





