مشاركة
0
/5
(
0
)
في السنوات الأخيرة، أصبحت العناوين التي تتحدث عن هجمات ضخمة على العملات الرقمية وأخبار سرقات العملات الرقمية شائعة بشكل مزعج.
في أحد هذه الحوادث الأخيرة، تعرضت منصة تداول العملات الرقمية الهندية WazirX لاختراق كبير في يوليو 2024، مما أدى إلى خسارة حوالي 234.9 مليون دولار من أموال المستثمرين. وتوقفت المنصة عن العمل بعد الهجوم.
وراء العديد من هذه الحوادث البارزة يكمن نموذج أعمال قد يبدو غير معتاد للكثيرين: البرمجيات الخبيثة كخدمة. يشرح هذا المقال كيفية عمل هذه المنصات، ويفحص تطور تطوير وتوزيع البرمجيات الخبيثة، ويناقش الآثار المترتبة على الشركات والمجتمع.
النقاط الرئيسية
تُمكّن خدمة البرمجيات الخبيثة كخدمة حتى المجرمين غير التقنيين من شن هجمات معقدة.
يستفيد مجرمو الإنترنت من عروض CaaS المتنوعة، بما في ذلك برامج الفدية، وأطقم التصيد الاحتيالي، وشبكات البوت، وأطقم الاستغلال، لشن هجمات واسعة النطاق بجهد ضئيل.
تلعب العملات الرقمية دورًا هامًا في جرائم الإنترنت الحديثة، إذ توفر الخصوصية، والوصول العالمي، والسيولة العالية لغسيل الأموال المسروقة.
ما هي البرمجيات الخبيثة كخدمة؟
البرمجيات الخبيثة كخدمة (CaaS) هي نموذج أعمال يقوم فيه مجرمو الإنترنت ببيع أو تأجير البرمجيات الخبيثة وأدوات الاختراق الجاهزة، على غرار خدمات الاشتراك. يمكن لأي شخص حتى لو لم يكن لديه مهارات حاسوبية متقدمة أن يدفع ثمن أداة تساعده على اختراق الأنظمة الحاسوبية، أو سرقة البيانات، أو اختطاف محافظ العملات الرقمية.
استخدمت مجموعة مجرمي الإنترنت الشهيرة المعروفة باسم Evil Corp البرمجيات الخبيثة المستأجرة لشن هجمات برامج الفدية التي كلفت الشركات ملايين الدولارات. وهذا يوضح كيف يمكن للمجرمين الأقل مهارة تقنيًا أن يتسببوا في أضرار جسيمة ببساطة من خلال الاستفادة من هذه الخدمات.
كيف بدأت الأمور؟
لقد تغيرت جرائم الإنترنت كثيرًا مع تقدم التكنولوجيا. ففي الأيام الأولى، كان الهاكرز غالبًا ما يصنعون فيروسات ودودات بسيطة يدويًا. وكانت هذه البرامج المبكرة تُكتب عادةً بواسطة هواة أو مجموعات صغيرة وتنتشر بشكل عشوائي، غالبًا مستغلة الثغرات التي لم يكن الكثيرون على دراية بها.
بحلول أوائل العقد الأول من القرن الحادي والعشرين، أصبح مجرمو الإنترنت أكثر تنظيماً. لم يعد الأمر يقتصر على إثارة الفوضى فحسب، بل أصبح يتعلق بسرقة الأموال والبيانات وحتى الهويات. على سبيل المثال، ظهر حصان طروادة المصرفي "زيوس" حوالي عام 2007 واستخدم لسرقة بيانات الاعتماد المصرفية من آلاف المستخدمين حول العالم.
وفي نفس الفترة، بدأت تظهر عمليات التصيد الاحتيالي وأشكال مبكرة من هجمات برامج الفدية، مما يدل على تحول واضح نحو هجمات إلكترونية بدوافع مالية.
اليوم، أصبح المشهد أكثر تعقيدًا. حيث تقدم بعض الخدمات السرية خدمات برمجيات خبيثة لمساعدة عملائها في إدارة عمليات الاختراق الخاصة بهم، وحل المشكلات، وحتى تقديم النصائح حول كيفية التهرب من تطبيق القانون.
وبهذه الطريقة، تطورت البرمجيات الخبيثة كخدمة من ممارسة متخصصة إلى صناعة تحت الأرض متكاملة تحاكي نماذج دعم التكنولوجيا وتسليم البرمجيات الشرعية.
نظام البرمجيات الخبيثة والجهات الفاعلة الرئيسية
يُعد نظام البرمجيات الخبيثة شبكة معقدة من أصحاب المصلحة المتنوعين، حيث يلعب كل منهم دورًا مميزًا.
المشغلون والمطورون: من جهة، يوجد المطورون الذين يقضون الكثير من الوقت والمال في إنشاء برمجيات خبيثة متطورة. يقومون بتصميم برمجياتهم لتخطي برامج مكافحة الفيروسات العادية وغيرها من أنظمة الأمان.
الوسطاء والمعلنين: يساعد الوسطاء والمروجون في ربط هؤلاء المطورين بالمستخدمين النهائيين. إنهم يسهلون المعاملات باستخدام رسائل مشفرة وطرق دفع مجهولة الهوية، مثل العملات الرقمية، كما هو موضح في طرق الدفع.
المشترون: يمكن أن يتراوح عملاء شراء هذه الخدمات من مجرمين عاديين إلى مجموعات جرائم إلكترونية منظمة تخطط لهجمات كبرى.
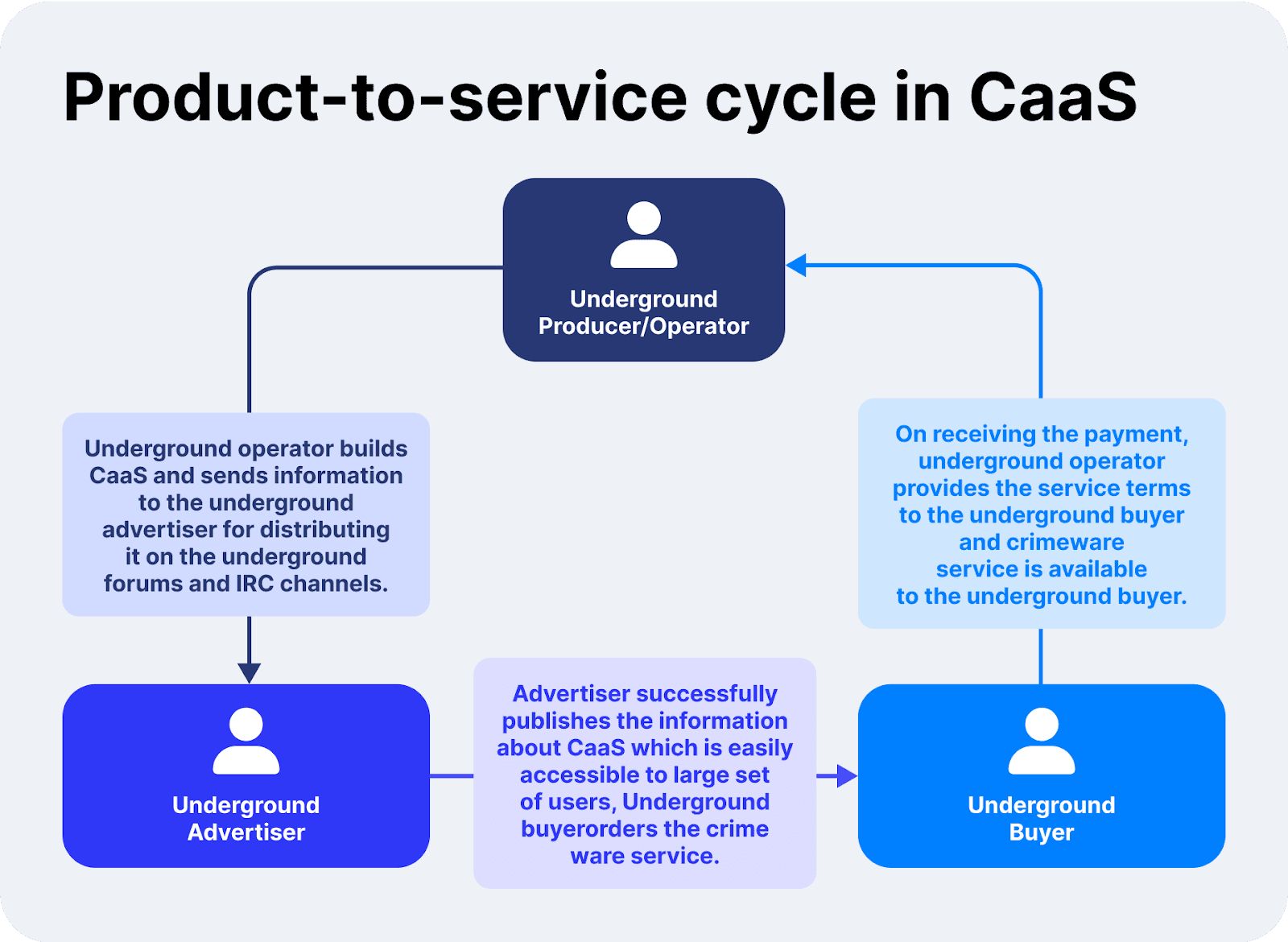
أنواع خدمة البرمجيات الخبيثة كخدمة (CaaS)
على غرار منصات SaaS الشرعية، تقدم حلول CaaS اشتراكات أو نماذج دفع حسب الاستخدام أو مشتريات لمرة واحدة:
برمجيات الفدية كخدمة (RaaS)
يمكن القول إن RaaS أصبح الجزء الأكثر شهرة في نظام جرائم الإنترنت. تمكّن منصات RaaS حتى أولئك الذين لديهم معرفة تقنية بسيطة من شن هجمات برامج الفدية.
تعمل العديد من منصات RaaS بنموذج الشراكة، حيث يحصل المشغلون على جزء من مدفوعات الفدية مقابل توفير أداة برامج الفدية. غالبًا ما يتمكن المستخدمون من تعديل مذكرات الفدية، وطرق التشفير، وتعليمات الدفع لتخصيص الهجمات لأهداف محددة.
خدمة استئجار هجمات الحرمان من الخدمة الموزعة (DDoS)
تتيح خدمات استئجار هجمات DDoS، المعروفة أيضًا باسم "بوتر" أو "ستريسر"، للعملاء استئجار شبكات من الأجهزة المخترقة (أو الاستفادة من البنى التحتية القائمة على السحابة) لشن هجمات DDoS واسعة النطاق.
وقد تم استخدام هذه الخدمات لاستهداف الشركات والمؤسسات السياسية وحتى البنى التحتية الحيوية. لقد أدت سهولة استخدامها وتوفرها إلى زيادة ملحوظة في وتيرة وحجم هجمات DDoS على مستوى العالم.
أطقم التصيد الاحتيالي وخدمات انتحال البريد الإلكتروني
يظل التصيد الاحتيالي أحد أقدم وأكثر الطرق فعالية لمجرمي الإنترنت. تُبسط أطقم التصيد الاحتيالي إنشاء مواقع إلكترونية احتيالية ورسائل بريد إلكتروني مخادعة تهدف إلى جمع المعلومات الحساسة.
لقد قللت أطقم التصيد الاحتيالي من حاجز الدخول لشن حملات التصيد، مما ساهم في ارتفاع معدلات سرقة الهوية والاحتيال المالي وتسرب البيانات.
أطقم الاستغلال
أطقم الاستغلال هي مجموعات من الأدوات البرمجية المصممة لتحديد واستغلال الثغرات في الأنظمة والبرمجيات. تعمل هذه الأطقم على أتمتة عملية الاستغلال، مما يجعل من الممكن اختراق الأنظمة دون تدخل يدوي.
لقد أدى الأتمتة التي توفرها أطقم الاستغلال إلى تضخيم حجم وسرعة الهجمات الإلكترونية بشكل كبير. وتظل المؤسسات التي تفشل في الحفاظ على تحديث البرمجيات وتصحيحات الأمان عرضة لخطر كبير.
خدمات شبكات البوت
تتيح خدمات شبكات البوت لمجرمي الإنترنت التحكم في شبكات من الأجهزة المخترقة، أو "بوتات"، لتنفيذ مجموعة متنوعة من الأنشطة الخبيثة تتراوح من هجمات DDoS إلى توزيع الرسائل المزعجة.
تُعد شبكات البوت متعددة الاستخدامات بشكل مذهل ويمكن استخدامها في مجموعة من متجهات الهجوم. إن طبيعتها الموزعة تجعل من الصعب على الجهات الأمنية وفرق الأمن السيبراني تفكيكها، خاصة مع استمرار تطور البرمجيات الخبيثة الأساسية.
أطقم تطوير البرمجيات الخبيثة (MDKs)
توفر أطقم تطوير البرمجيات الخبيثة (MDKs) الأدوات والأطر اللازمة لتطوير برمجيات خبيثة مخصصة بسرعة. تقوم هذه الأطقم بتبسيط جزء كبير من تعقيد البرمجة، مما يمكّن حتى المبتدئين من إنتاج برمجيات خبيثة متطورة.
لقد أدى توفر أطقم تطوير البرمجيات الخبيثة إلى انتشار واسع لمتغيرات البرمجيات الخبيثة المخصصة. وهذا لا يزيد فقط من حجم التهديدات بل يعقد أيضًا جهود الكشف والتخفيف، حيث قد يتطلب كل متغير جديد نهجًا فريدًا لمواجهته.
خدمات مسجلات المفاتيح وبرمجيات التجسس
تُعد مسجلات المفاتيح وبرمجيات التجسس أدوات مصممة لمراقبة وتسجيل نشاط المستخدم على الأجهزة المصابة. تُعتبر هذه الخدمات حيوية لمجرمي الإنترنت المشاركين في سرقة البيانات والتجسس.
تتميز مسجلات المفاتيح وبرمجيات التجسس بسهولة نشرها، مما يجعلها شائعة لسرقة الهوية والتجسس الصناعي. تتيح طبيعتها المتخفية إجراء مراقبة مطولة، مما يزيد من احتمال حدوث خسائر كبيرة في البيانات.
البنية التحتية التقنية والعروض المقدمة
غالبًا ما تكون البنية التحتية التقنية وراء هذه الخدمات متطورة بشكل ملحوظ. يستثمر مقدمو خدمات البرمجيات الخبيثة في تطوير برمجيات خبيثة معيارية وسهلة التحديث. ويقدمون ميزات مثل:
الأتمتة: للتعامل مع المهام المتكررة مثل البحث عن الثغرات أو توزيع البرمجيات الخبيثة.
تقنيات الإخفاء: لإخفاء الشفرة الخبيثة عن برامج مكافحة الفيروسات التقليدية.
التشفير وDNS سريع التدفق: لجعل تتبع وإيقاف خوادم القيادة والتحكم (C2) أكثر صعوبة على المتخصصين في الأمن.
يرافق العديد من هذه الخدمات لوحات تحكم تتابع نجاح الهجمات، على غرار منصات التحليل الشرعية.
كيف ينشر مجرمو الإنترنت البرمجيات الخبيثة؟
طور مجرمو الإنترنت عدة طرق لنشر البرمجيات الخبيثة بكفاءة:
حملات التصيد الاحتيالي: تخدع هذه الهجمات المستخدمين للنقر على روابط خبيثة أو تنزيل مرفقات مصابة. ولا يزال التصيد أحد أكثر الطرق شيوعًا وفعالية لتوزيع البرمجيات الخبيثة.
الإعلانات الخبيثة: يقوم مجرمو الإنترنت بإدخال إعلانات خبيثة في شبكات الإعلانات الشرعية. وعندما ينقر المستخدمون على هذه الإعلانات، قد يقومون بتنزيل البرمجيات الخبيثة دون علمهم.
أطقم الاستغلال: هي أدوات تقوم بمسح نظام المستخدم تلقائيًا بحثًا عن الثغرات. وبمجرد العثور على ثغرة، يقوم طقم الاستغلال بتوصيل حمولة البرمجيات الخبيثة دون أي تفاعل إضافي من المستخدم.
الهندسة الاجتماعية: إلى جانب الاستغلال التقني، يستخدم مجرمو الإنترنت في كثير من الأحيان التلاعب النفسي لإقناع المستخدمين بأداء إجراءات تعرض أمنهم للخطر. وقد يتضمن ذلك تنبيهات زائفة، أو رسائل عاجلة، أو انتحال هوية منظمات موثوقة.
يُقلل توفر الأدوات المؤتمتة والتعليمات التفصيلية من المخاطر على المهاجم ويزيد من مدى وصول حملاته.
دور البلوك تشين في جرائم الإنترنت الحديثة
لقد أعادت العملات الرقمية تشكيل المشهد المالي بشكل جذري من خلال تقديم طرق جديدة لنقل وتخزين القيمة. وللأسف، جذبت هذه الابتكارات مجرمي الإنترنت، مما جعلها هدفًا رئيسيًا لعمليات البرمجيات الخبيثة كخدمة.
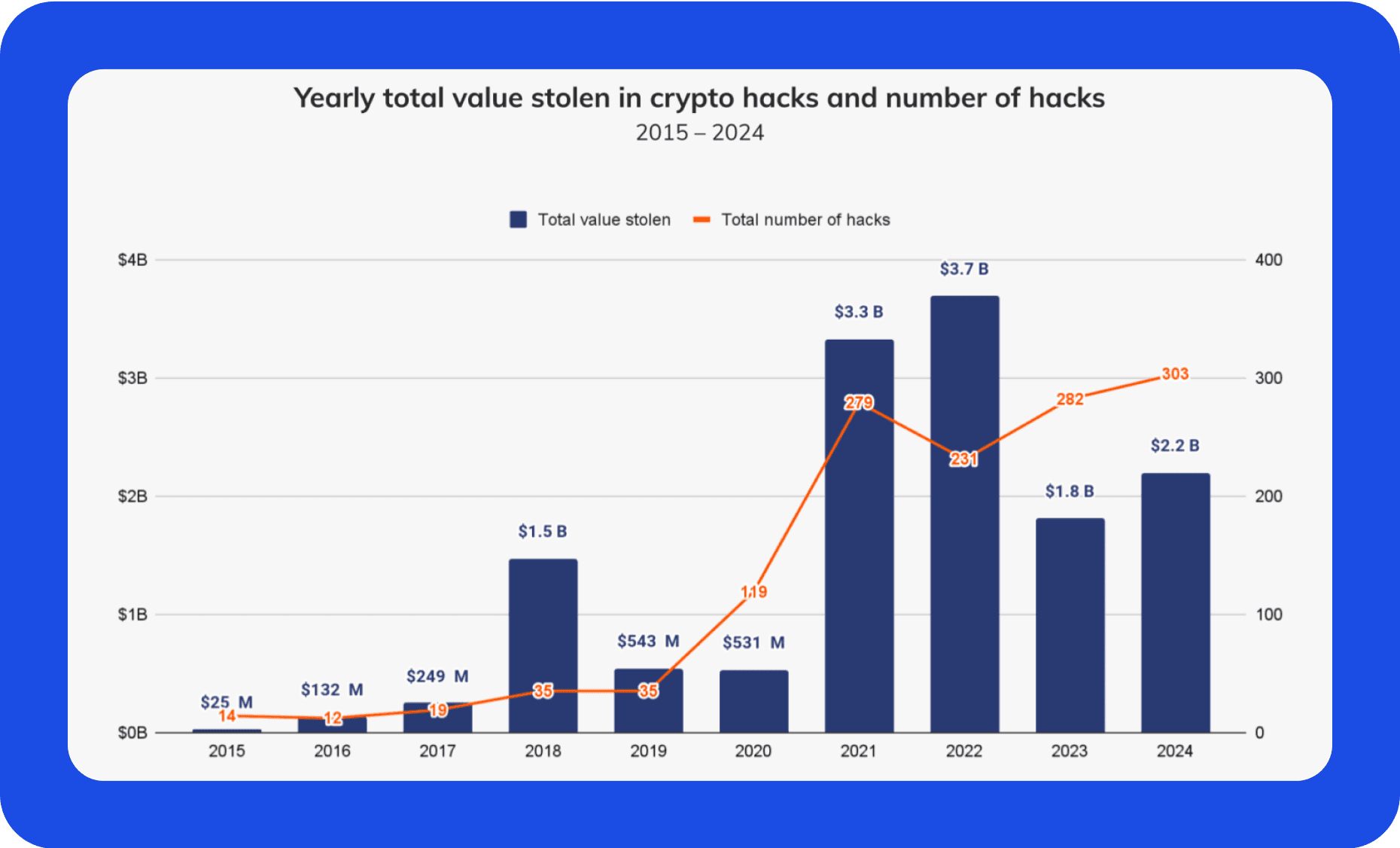
تقدم الأصول الرقمية العديد من المزايا لمجرمي الإنترنت:
الخصوصية: المعاملات في العديد من العملات الرقمية تكون ذاتية الهوية، مما يصعب على السلطات تتبع الأموال.
القبول العالمي: تعمل العملات الرقمية على نطاق عالمي دون الحاجة لوسطاء مثل البنوك. وهذا يعني أنه يمكن تحويل أو غسيل الأموال المسروقة بسرعة.
سهولة الوصول: المحافظ الرقمية ومنصات التبادل متاحة على مدار الساعة طوال أيام الأسبوع، وكثير منها يفتقر إلى تدابير أمان قوية مقارنة بالمؤسسات المالية التقليدية.
سيولة عالية: بمجرد سرقتها، يمكن تحويل العملات الرقمية بسرعة إلى نقود أو استخدامها لشراء السلع، وغالبًا ما تترك آثارًا ضئيلة.
تخلق هذه العوامل بيئة مثالية لازدهار خدمات البرمجيات الخبيثة. يمكن لمجرمي الإنترنت استئجار الأدوات اللازمة لاختراق المحافظ الرقمية ومنصات التبادل، مع العلم بأن العائد المحتمل كبير للغاية.
التأثير على الشركات والمجتمع
تمتد عواقب البرمجيات الخبيثة كخدمة إلى ما هو أبعد من الحوادث الفردية للجرائم الإلكترونية. فالتأثيرات تُشعر بها عبر الاقتصاد والمجتمع، مما يمثل تحديًا للمؤسسات الخاصة والحكومية على حد سواء.
التداعيات الاقتصادية والأمنية
يمكن أن تكون الخسائر المالية الناتجة عن الهجمات الإلكترونية ضخمة. عندما تتسلل البرمجيات الخبيثة إلى شبكات الشركات، يمكن أن تؤدي إلى:
الخسائر المالية المباشرة: من خلال المعاملات الاحتيالية أو مطالبات برامج الفدية.
سرقة الملكية الفكرية: فقدان البيانات الحساسة يمكن أن يؤدي إلى حدوث عيوب تنافسية.
تعطيل العمليات: يمكن أن يؤدي التوقف عن العمل وانقطاع الأنظمة إلى شل عمليات الأعمال، مما يؤدي إلى خسائر إيرادات كبيرة.
تكون المخاطر أكبر بكثير بالنسبة للمؤسسات المالية ومنصات تبادل العملات الرقمية. فقد يؤدي هجوم ناجح واحد إلى تقويض ثقة العملاء والإضرار بسمعة العلامة التجارية لفترة طويلة.
التحديات التي تواجه الدفاع السيبراني
غالبًا ما تواجه التدابير التقليدية للأمن السيبراني صعوبة في مواكبة التطور السريع للبرمجيات الخبيثة. وقد وجدت العديد من المؤسسات أن حلول مكافحة الفيروسات التقليدية والجدران النارية غير كافية للحماية من أحدث التكتيكات التي يستخدمها مجرمو الإنترنت. وقد أدى ذلك إلى زيادة الطلب على منصات خدمات الدفاع ضد التهديدات الإلكترونية المتقدمة.
تستخدم هذه الحلول الأمنية الحديثة:
التحليل السلوكي لاكتشاف الأنماط غير المعتادة في حركة المرور على الشبكة.
الكشف عن التهديدات المدعوم بالذكاء الاصطناعي الذي يمكنه التكيف مع الأشكال الجديدة من البرمجيات الخبيثة في الوقت الفعلي.
معلومات التهديد المتكاملة التي تشمل تبادل البيانات بين المؤسسات لإنشاء استراتيجية دفاعية أكثر استباقية.
على الرغم من هذه التطورات، لا يزال الصراع المستمر بين المهاجمين والمدافعين قائماً. يقوم مجرمو الإنترنت باستمرار بتكييف تقنياتهم لتجاوز التدابير الأمنية الجديدة، مما يتطلب ابتكارًا مستمرًا في دفاعات الأمن السيبراني.
الآثار الاجتماعية
يمكن أن تؤدي الهجمات الإلكترونية إلى تآكل ثقة الجمهور في الخدمات الرقمية والمؤسسات المالية. ومع زيادة وعي المستهلكين بالمخاطر المرتبطة بالمعاملات عبر الإنترنت، قد يتباطأ تبني التقنيات المبتكرة. وهذا بدوره يمكن أن يؤثر على النمو الاقتصادي والتقدم التكنولوجي.
علاوة على ذلك، فإن الجرائم الإلكترونية عالمية، لذا لا توجد دولة محصنة. إن الطبيعة العابرة للحدود لهذه الهجمات تعقد جهود تطبيق القانون، مما يتطلب تعاونًا دوليًا لتعقب ومقاضاة مجرمي الإنترنت. وتُشعر آثار هذه التحديات على مستوى العالم بينما تعمل الدول معًا على تطوير أطر تنظيمية أقوى وتدابير أمن سيبراني أكثر فعالية.
استراتيجيات الدفاع السيبراني وأفضل الممارسات
نظرًا لتعقيد الهجمات الإلكترونية الحديثة، تحتاج المؤسسات إلى تبني نهج متعدد الطبقات للأمن السيبراني. فيما يلي بعض الاستراتيجيات وأفضل الممارسات التي يمكن أن تساعد في التخفيف من المخاطر التي تفرضها البرمجيات الخبيثة كخدمة.
تدريب الموظفين وزيادة الوعي
يمكن أن تساعد جلسات التدريب المنتظمة الموظفين على التعرف على محاولات التصيد الاحتيالي، والبريد الإلكتروني المشبوه، وغيرها من تكتيكات الهندسة الاجتماعية. غالبًا ما يكون الموظفون المطلعون خط الدفاع الأول.
تحديثات البرامج المنتظمة وترقيعات الأمان
تستغل العديد من الهجمات الثغرات المعروفة في البرمجيات. إن الحفاظ على تحديث الأنظمة بأحدث الترقيعات يمكن أن يقلل بشكل كبير من خطر الاستغلال.
تقسيم الشبكة
يمكن أن يساعد تقسيم شبكتك إلى أجزاء أصغر ومتحكم بها في احتواء الهجوم والحد من انتشار البرمجيات الخبيثة.
المصادقة متعددة العوامل (MFA)
يُصعّب تطبيق MFA على الأنظمة الحيوية على المهاجمين الحصول على وصول غير مصرح به، حتى وإن تمكنوا من سرقة بيانات تسجيل الدخول.
الاتجاهات الناشئة ومستقبل تطوير البرمجيات الخبيثة
يستمر مشهد الجرائم الإلكترونية في التطور، وكذلك الطرق التي يستخدمها من يقفون وراء البرمجيات الخبيثة كخدمة. هنا، نلقي نظرة على ما قد يحمله المستقبل ونلخص أهم رؤانا.
زيادة الأتمتة ودمج الذكاء الاصطناعي
مع تقدم الذكاء الاصطناعي، يستفيد منه كل من مجرمي الإنترنت والمتخصصين في الأمن السيبراني. في عالم الجريمة تحت الأرض، يمكن للبرمجيات الخبيثة المدعومة بالذكاء الاصطناعي أن تتكيف مع الدفاعات في الوقت الفعلي، مما يجعل من الصعب اكتشافها وتحييدها.
تعزيز استهداف الأصول المالية
مع الارتفاع المستمر في استخدام العملات الرقمية، من المتوقع زيادة في الهجمات المستهدفة على المحافظ الرقمية ومنصات التبادل. سيستمر مجرمو الإنترنت في تحسين تكتيكاتهم لتجاوز التدابير الأمنية واستغلال الثغرات في الأنظمة المالية الرقمية.
زيادة استخدام البنية التحتية اللامركزية
قد يتبنى مجرمو الإنترنت شبكات لامركزية تزيد من إخفاء أنشطتهم. من المرجح أن يشكل هذا الاتجاه تحديًا لأساليب تطبيق القانون التقليدية، مما يجعل التعاون الدولي أكثر أهمية.
أفكار ختامية
باختصار، تمثل البرمجيات الخبيثة كخدمة تحولًا جذريًا في مجال الجرائم الإلكترونية. فقد جعل التطور من هجمات فردية مخصصة إلى نموذج قائم على الخدمات منظمة للغاية، الهجمات الإلكترونية أكثر سهولة وتعقيدًا وتدميرًا من أي وقت مضى.
الأسئلة الشائعة
كيف ينشر مجرمو الإنترنت البرمجيات الخبيثة؟
يستخدم مجرمو الإنترنت طرقًا متنوعة لتوزيع البرمجيات الخبيثة، بما في ذلك رسائل التصيد الاحتيالي، والإعلانات الخبيثة (malvertising)، وأطقم الاستغلال، والهندسة الاجتماعية. تخدع هذه التقنيات المستخدمين لتنزيل ملفات مصابة أو النقر على روابط خبيثة، مما يمنح المهاجمين الوصول إلى أنظمتهم.
كيف تعمل البرمجيات الخبيثة كخدمة (CaaS)؟
تعمل CaaS مثل نموذج أعمال يعتمد على الاشتراك، حيث يستأجر أو يشتري مجرمو الإنترنت أدوات البرمجيات الخبيثة من الأسواق السرية. توفر هذه الخدمات برامج الفدية، وشبكات البوت، وأطقم التصيد الاحتيالي، وغيرها، مما يمكّن حتى المهاجمين غير الماهرين من شن هجمات إلكترونية معقدة.
ما هي الجريمة الإلكترونية في سياق الأمن السيبراني؟
تشير الجريمة الإلكترونية إلى الأنشطة غير القانونية التي تُجرى باستخدام التكنولوجيا الرقمية، وغالبًا ما تستهدف الأفراد أو الشركات أو الحكومات. يشمل ذلك الاختراق، وسرقة الهوية، وهجمات برامج الفدية، والاحتيال، وكلها تستغل الثغرات في الأنظمة والشبكات الحاسوبية.
ما هي أكثر الجرائم الإلكترونية شيوعًا؟
يعد التصيد الاحتيالي، ورسائل النصية الاحتيالية (smishing)، وانتهاك بريد الشركات (BEC) من بين أكثر الجرائم الإلكترونية شيوعًا. ففي عام 2023، أفادت 76% من المؤسسات حول العالم بأنها واجهت هجمات تصيد، في حين تعرض ما يقرب من ثلاثة أرباعها لعمليات احتيال عبر الرسائل النصية.
اقرأ أيضًا





