Share
0
/5
(
0
)
In the fast-paced and high-stakes world of trading, where sensitive financial data and transactions flow continuously, web server security is paramount. Trading companies are not just businesses; they are custodians of trust, safeguarding client investments and critical market information.
However, with great value comes great risk. Cybercriminals are constantly devising sophisticated attacks, targeting vulnerabilities of trading web servers and hosts to disrupt operations, steal data, or manipulate financial outcomes. Thus, how can the web server be protected from these problems?
This article intends to explain what web server security is and what its characteristics are. You will also learn what typical security concerns a trading web service has and how to avoid them.
Key Takeaways
Trading companies are high-value targets for cyberattacks due to their management of sensitive financial data and big funds reserves.
DDoS attacks are designed to overwhelm server resources, rendering the server non-functional.
SQL injection and DDoS attacks are among the most frequent challenges web servers face in the trading industry.
What Does Secure Web Server Stand For?
A secure server refers to a computer system or hosting environment configured to safeguard its data, operations, and communications from unauthorised access, breaches, and malicious activities. It is designed with security measures to ensure the confidentiality, integrity, and availability of the data and applications it hosts.
In addition to technical safeguards, a secure web server incorporates robust administrative and operational practices to enhance its protection. This includes implementing strict access policies, regular security audits, and continuous monitoring for unusual activities or vulnerabilities.
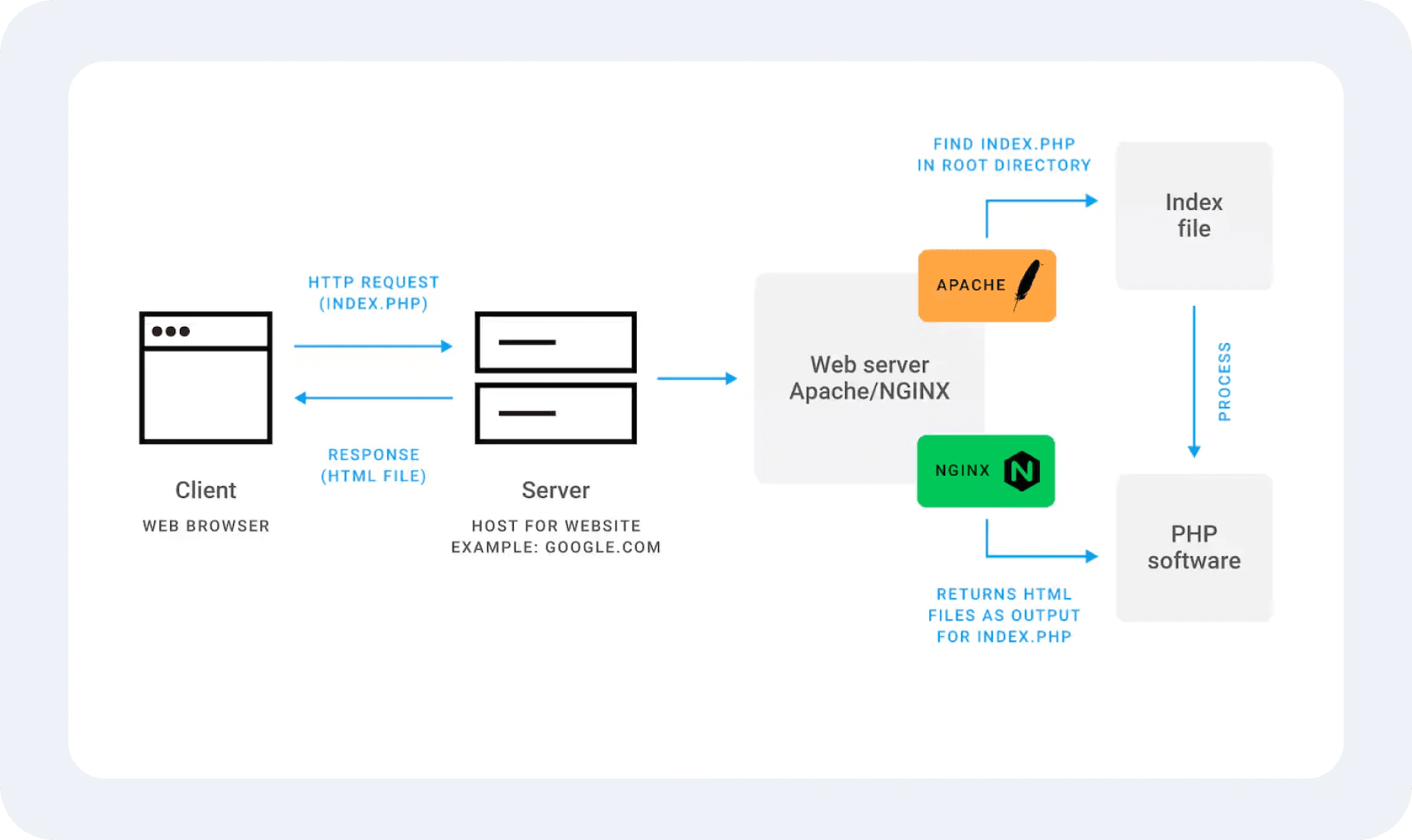
Secure servers often have failover mechanisms and disaster recovery plans to ensure business continuity, even during an attack or system failure.
By proactively addressing both internal and external threats, a secure server provides a reliable foundation for sensitive operations such as financial transactions, personal data management, and critical business processes.
[aa quote-global]
Fast Fact
Firewalls are crucial for server security, offering an extra layer of protection even when internal security features are in place.
[/aa]
Key Characteristics of a Secure Server
A secure server protects data, communications, and services from unauthorised access, breaches, and disruptions. Below are the essential characteristics that ensure a server remains secure:
Data Encryption
All communications between the web server and users are encrypted using SSL/TLS protocols to secure data from interception and tampering during transmission. This ensures all HTTPS connections, protecting against man-in-the-middle (MITM) attacks. Modern servers should support the latest TLS versions (e.g., TLS 1.3) for stronger encryption and faster performance.
Sensitive data stored on the server is encrypted using advanced encryption standards such as AES-256. This means that even if physical storage devices (e.g., hard drives) are compromised, the data remains unreadable without the encryption key. Servers may also use full-disk encryption for added protection.
Access Control
Permissions are strictly assigned based on job functions. For instance, database administrators may only access database servers, while developers may have access to application servers but not production systems. This segmentation reduces the risk of insider threats.
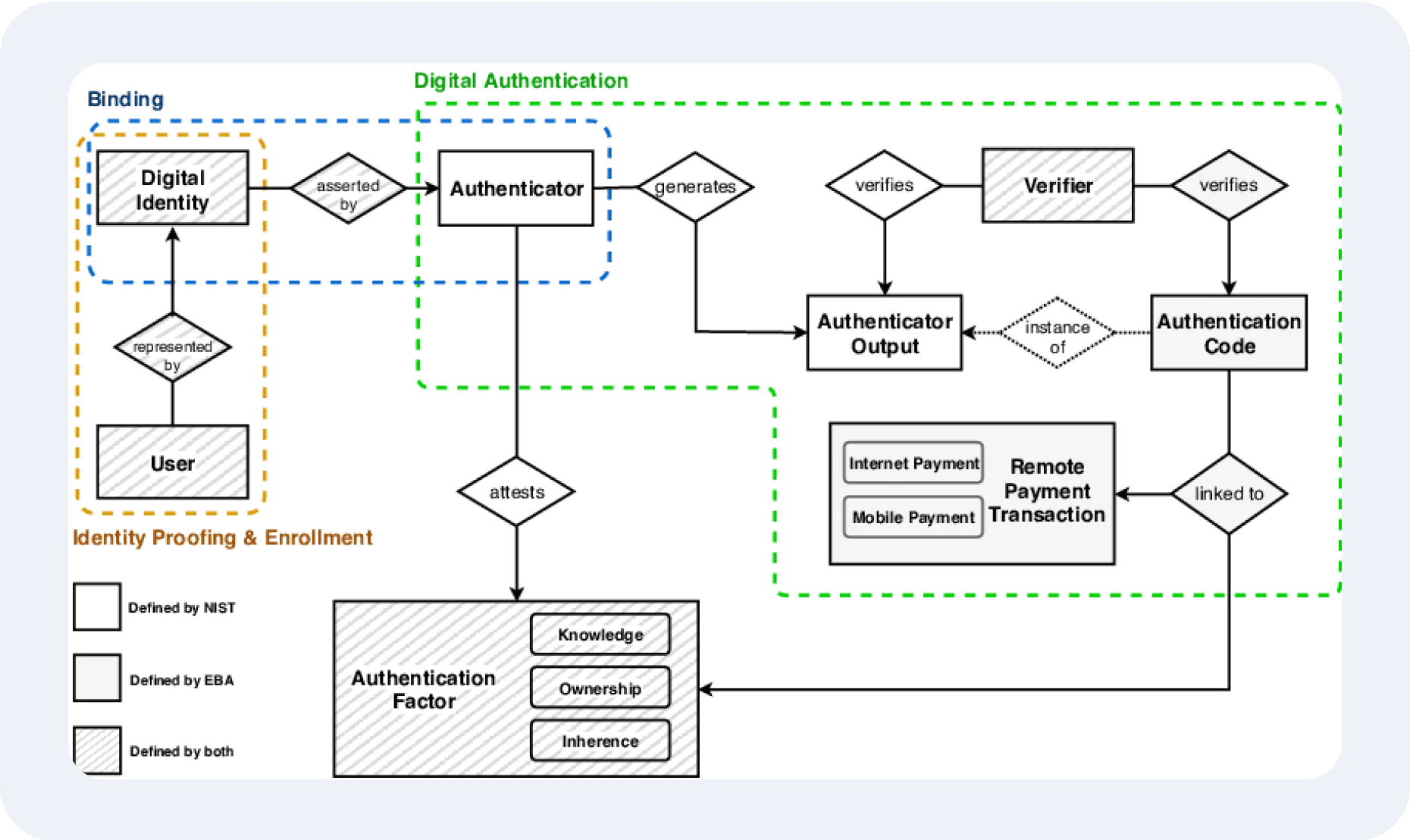
An MFA system, on the other hand, combines something the user knows (e.g., password), something they have (e.g., a mobile device or security token), and sometimes something they are (e.g., biometrics). MFA drastically reduces the success rate of credential-stealing attacks like phishing.
Firewall Protection
Network firewalls filter traffic based on predetermined security rules, such as IP whitelisting, blacklisting, and blocking traffic from certain regions known for malicious activities. Advanced firewalls may also integrate intrusion detection and prevention capabilities.
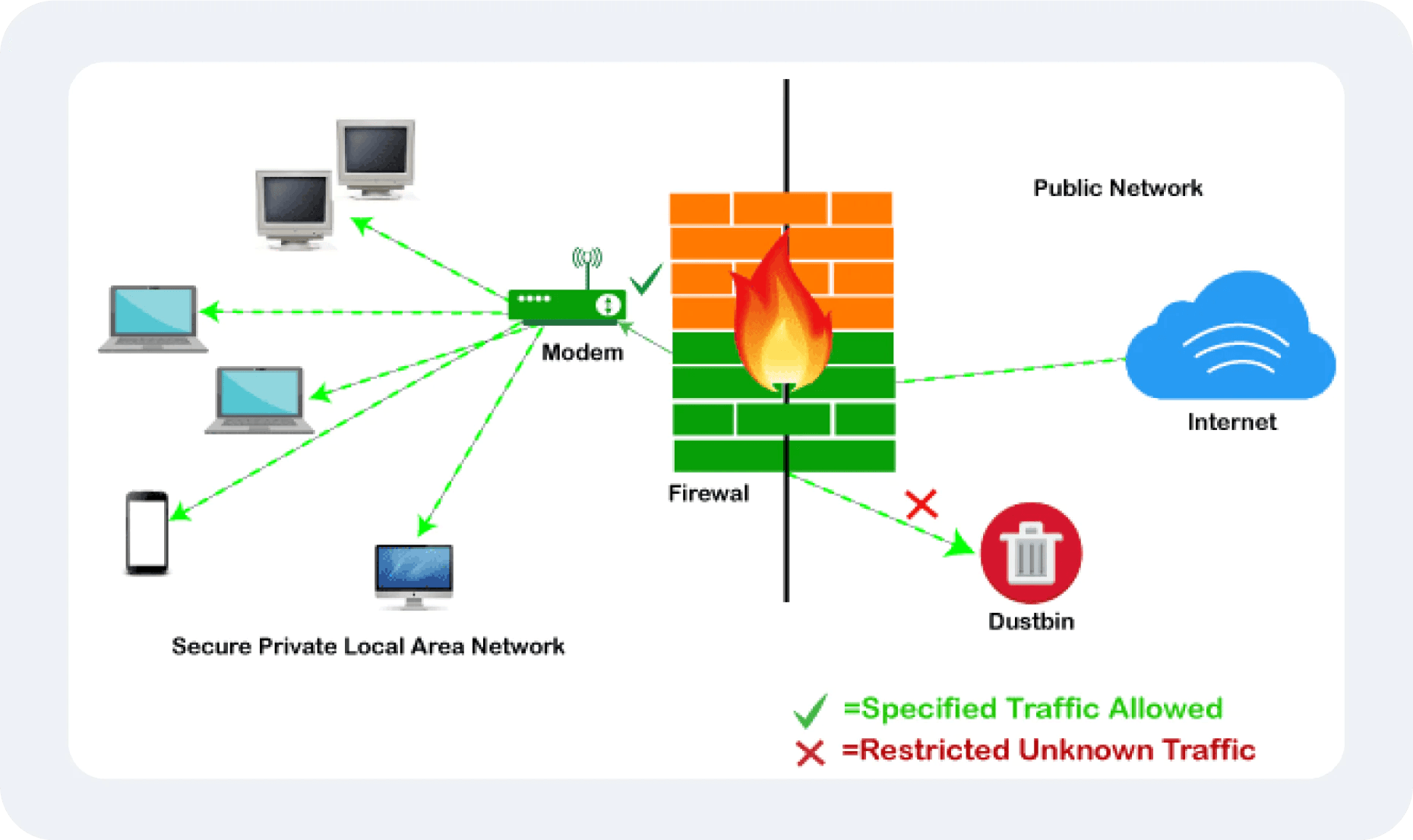
Web application firewalls specialise in inspecting HTTP/HTTPS requests to detect and block attacks targeting web applications, such as injections, cross-site scripting (XSS), and session hijacking. They also analyse incoming and outgoing data for abnormalities.
Regular Updates and Patch Management
Developers frequently release patches to fix vulnerabilities. Servers running outdated software are highly vulnerable to attacks, such as exploiting unpatched secondary vulnerabilities.
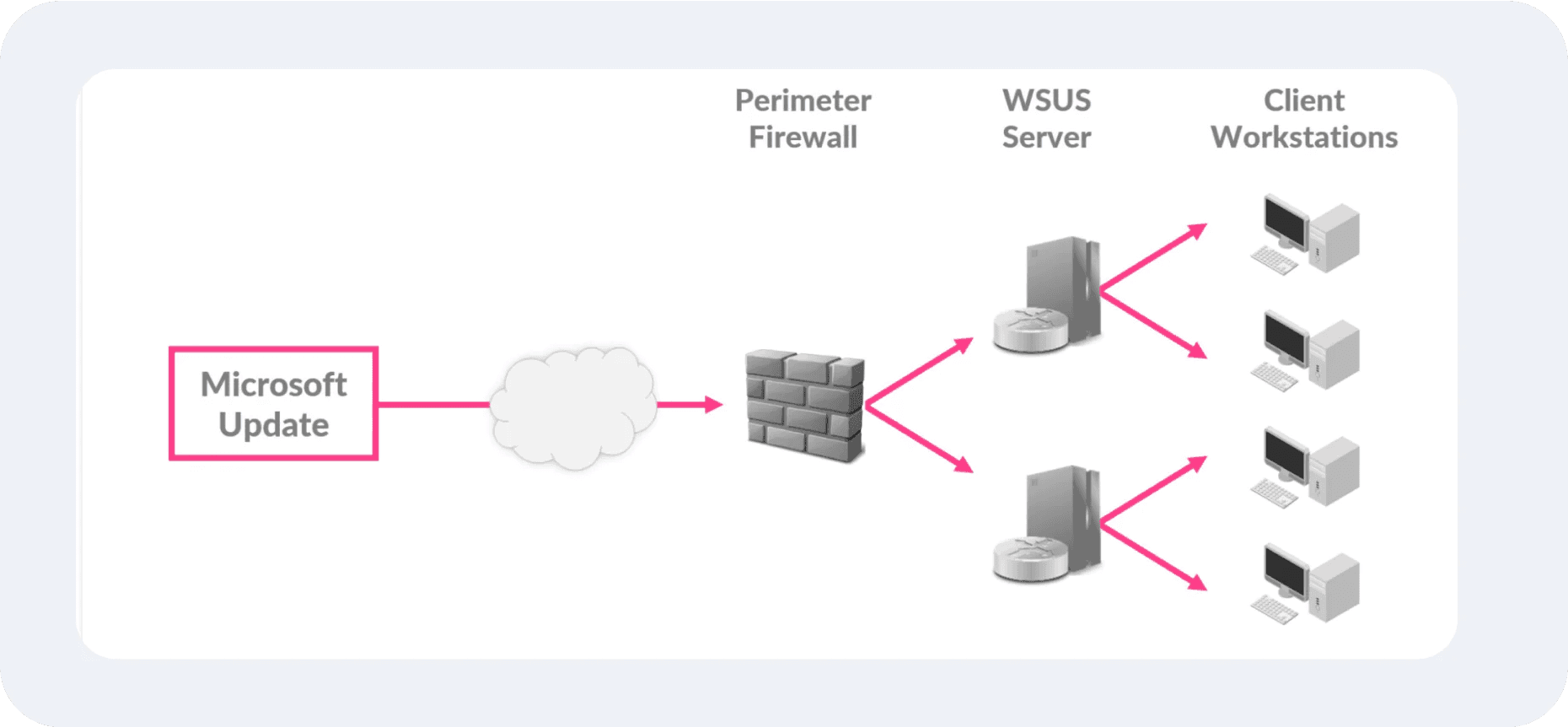
Tools like WSUS (Windows Server Update Services) or Ansible automate the patching process across multiple web servers, reducing administrative overhead and consistently applying updates.
Intrusion Detection and Prevention
Intrusion detection systems monitor and log traffic patterns, providing administrators with insights into suspicious activities such as unusual login attempts or a surge in bandwidth usage.
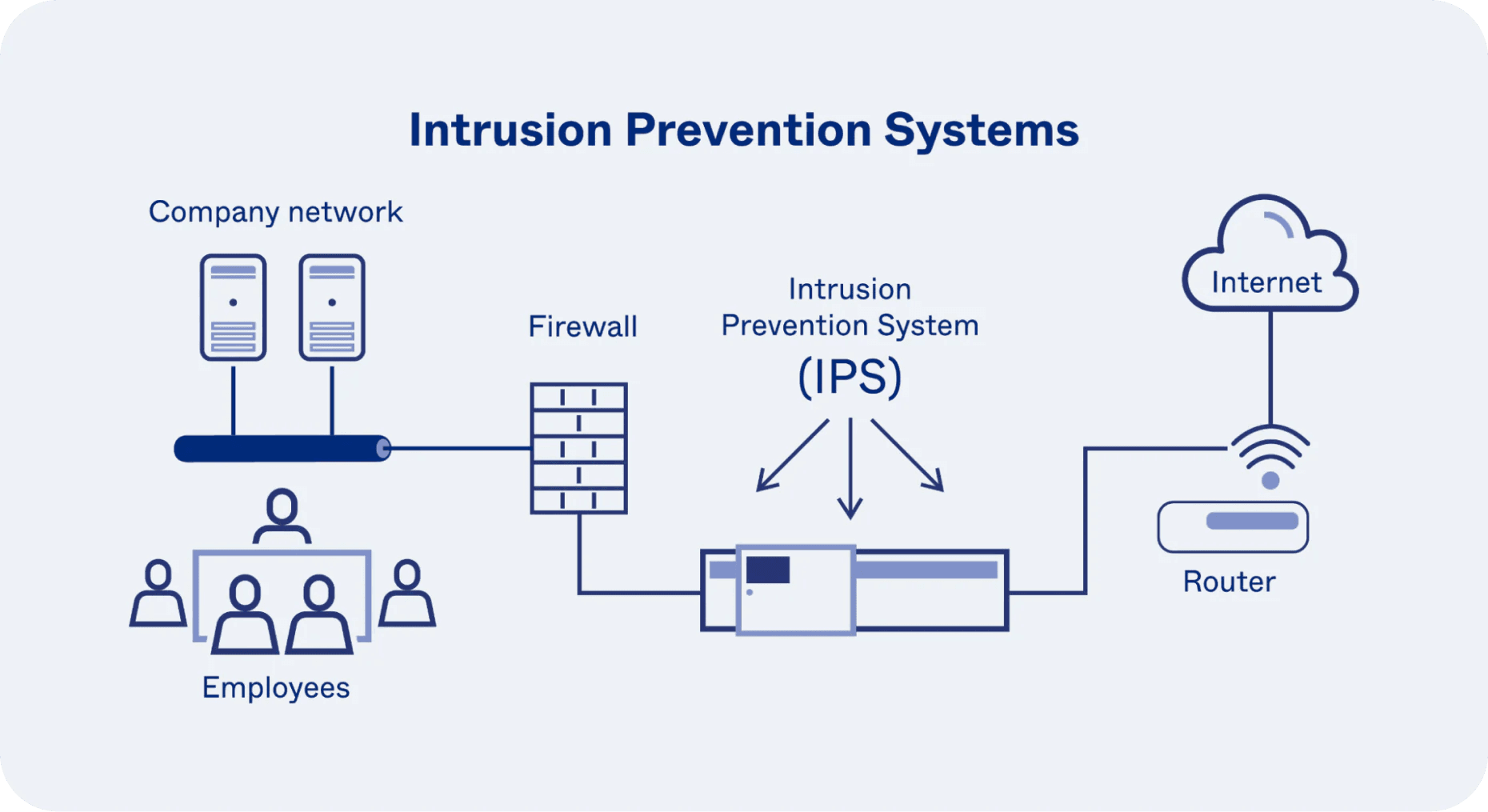
Intrusion prevention systems actively block malicious actions by identifying and responding to threats in real time. For example, it may automatically block IPs associated with brute-force login attempts or malware distribution.
Secure Configuration
Unsecured default settings, such as "admin/admin" login credentials or open administrative ports, are common entry points for attackers. Secure servers eliminate these vulnerabilities by requiring custom configurations during deployment.
Only necessary software, services, and ports are enabled. For instance, if a server doesn’t require FTP, it is disabled to reduce attack surfaces. Tools like Nmap can be used to scan for unexpected open ports periodically.
Backup and Disaster Recovery
Data is backed up at different intervals (e.g., daily, weekly) based on the criticality of the data. For example, transactional data for a trading company might require hourly backups.
Disaster recovery ensures that backups are stored separately from the primary web server. This protects against localised events, such as hardware failures or natural disasters. Backups are encrypted to maintain data security.
Comprehensive Monitoring and Logging
Logs capture user activities, changes to server settings, access attempts, and error reports. These logs are invaluable for forensic investigations following a breach.
Real-time monitoring tools use machine learning to detect anomalies, such as an unusual traffic volume from a single IP or attempts to access restricted files. Alerts are sent to administrators for immediate action.
Physical Security
Physical access to server rooms is restricted to authorised personnel using mechanisms like biometric scanners (fingerprint or retina) or secure access cards. Regular access reviews ensure only active staff have permissions.
Server rooms have CCTV, motion sensors, and alarms to prevent unauthorised entry. Environmental controls, such as fire suppression systems and temperature regulation, protect against physical damage.
Compliance with Security Standards
Secure servers align with frameworks like GDPR (data protection for EU residents), HIPAA (healthcare data security), PCI DSS (for handling credit card data), or SOX (financial reporting security in the U.S.).
Servers undergo regular third-party audits to ensure compliance. Certifications like ISO 27001 signal adherence to global information security best practices.
DDoS Protection
Tools like Cloudflare or Akamai filter and distribute incoming traffic across a network of servers, mitigating DDoS attacks by spreading the load.
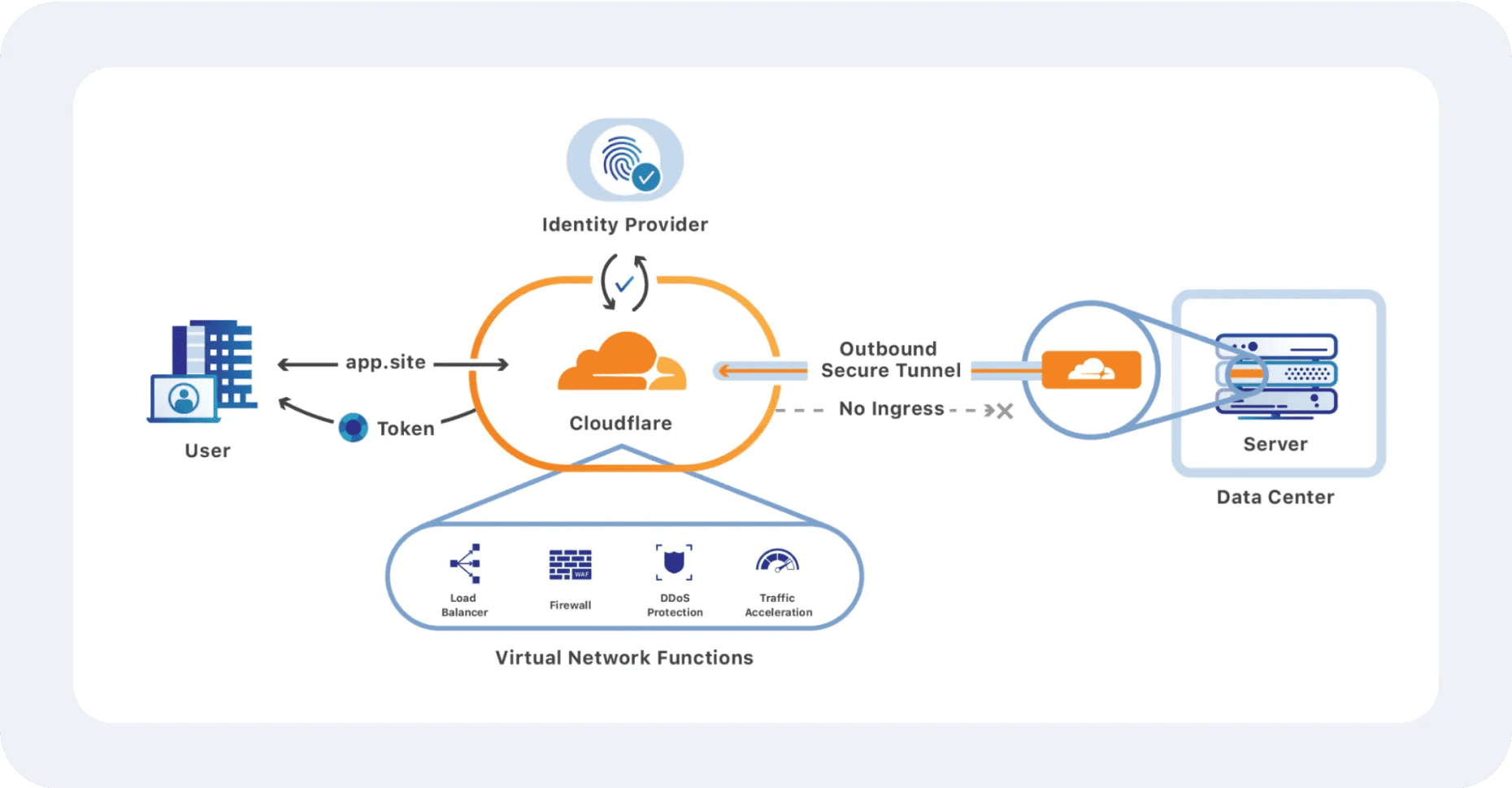
Also, load balancers distribute incoming requests across multiple servers, preventing any one server from becoming overwhelmed. They also offer redundancy, ensuring continuity during high traffic volumes or attacks.
High Availability and Redundancy
To perform redundancy, failover systems detect hardware or software failures and automatically switch to backup web servers or infrastructure, ensuring minimal downtime.
Furthermore, critical systems and data are replicated across multiple data centres in different locations, ensuring continuity even in cases of regional disasters like earthquakes or power outages.
Common Security Threats Faced by Web Servers
Web servers play a critical role in hosting websites and online services but are also prime targets for cyberattacks. These attacks can compromise data and services' confidentiality, integrity, and availability, causing severe consequences.
Below are the primary security risks and their implications:
Malware and Ransomware
Malicious software can infiltrate the server, often through email attachments, compromised websites, or vulnerabilities in software. Once installed, malware can steal data, disrupt operations, or encrypt files during a ransomware attack.
Sensitive data may be leaked, services may experience downtime, and organisations may face significant financial losses from ransom payments or operational disruptions. Reputational damage can also deter customers from trusting the service.
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
Attackers use overwhelming traffic to crash or slow down the web server, making it unusable for legitimate users. DDoS attacks are distributed across multiple sources, making them harder to mitigate.
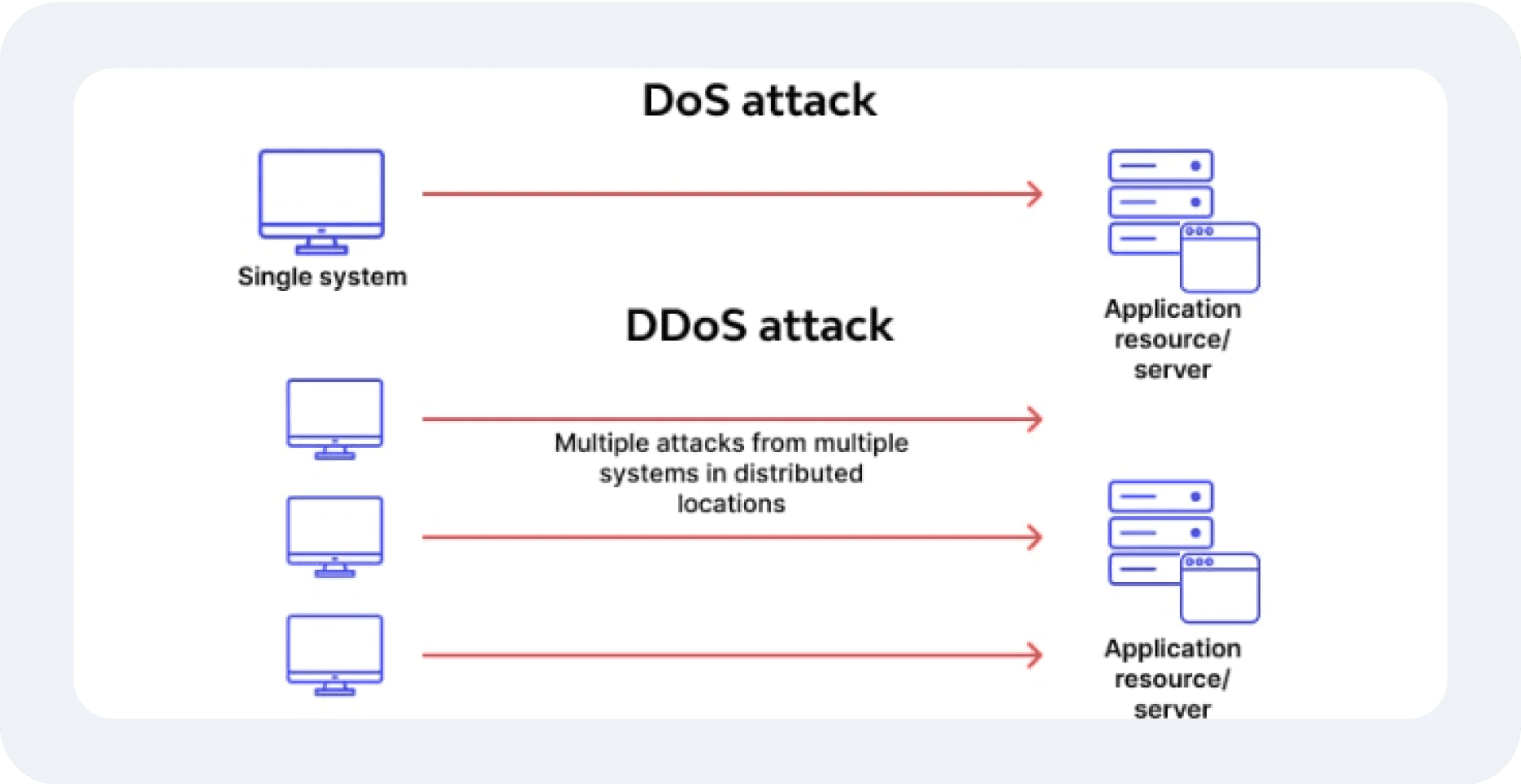
Prolonged downtime disrupts business operations, results in lost revenue, and damages customer trust. Recovery from a large-scale DDoS attack can also incur significant costs.
SQL Injection
Attackers exploit vulnerable input fields (e.g., login forms) to inject malicious SQL commands, which can give unauthorised access to sensitive database information.
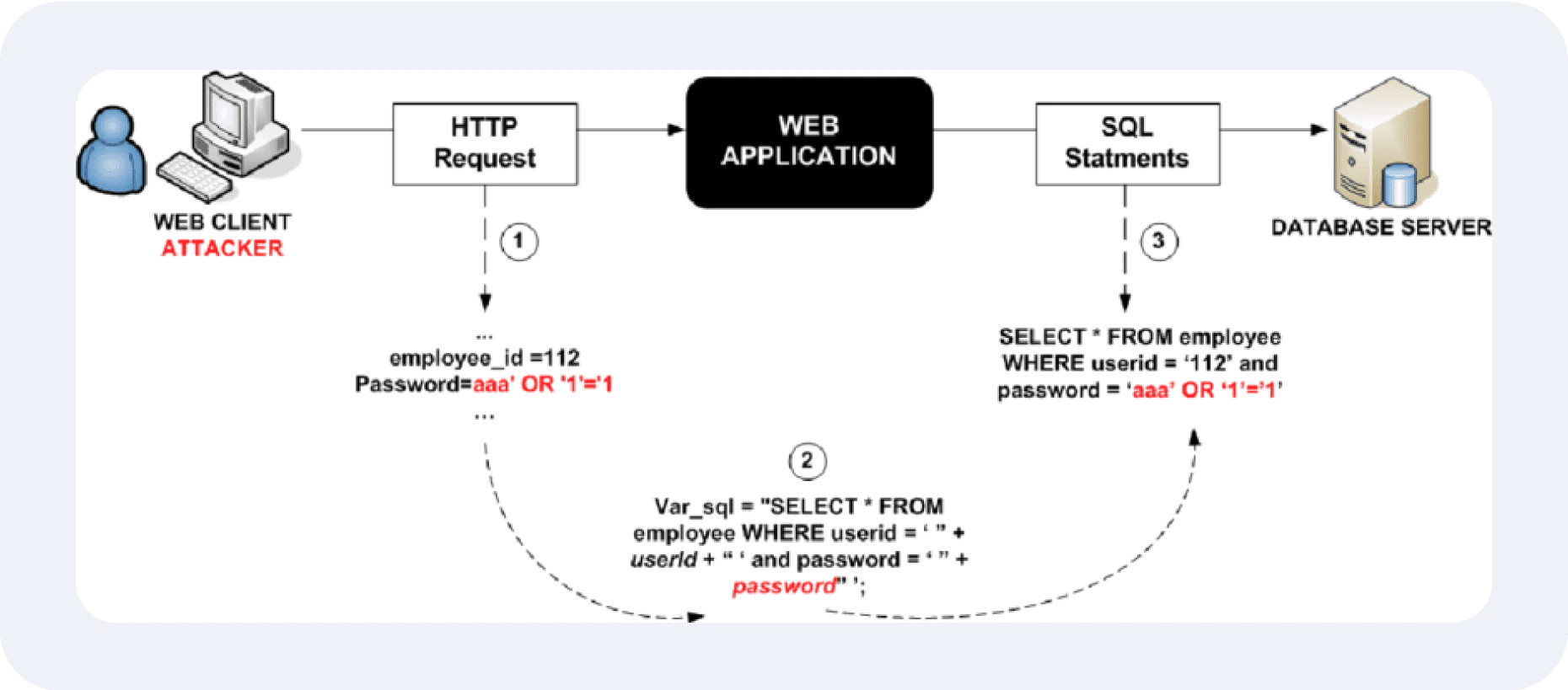
Attackers can steal, delete, or manipulate critical data, such as customer information or financial records. This type of breach often leads to regulatory penalties and loss of reputation.
Cross-Site Scripting (XSS)
Malicious scripts are injected into a website’s content, causing the browser of anyone visiting the site to execute the attacker’s code. Common targets include login pages and forms.
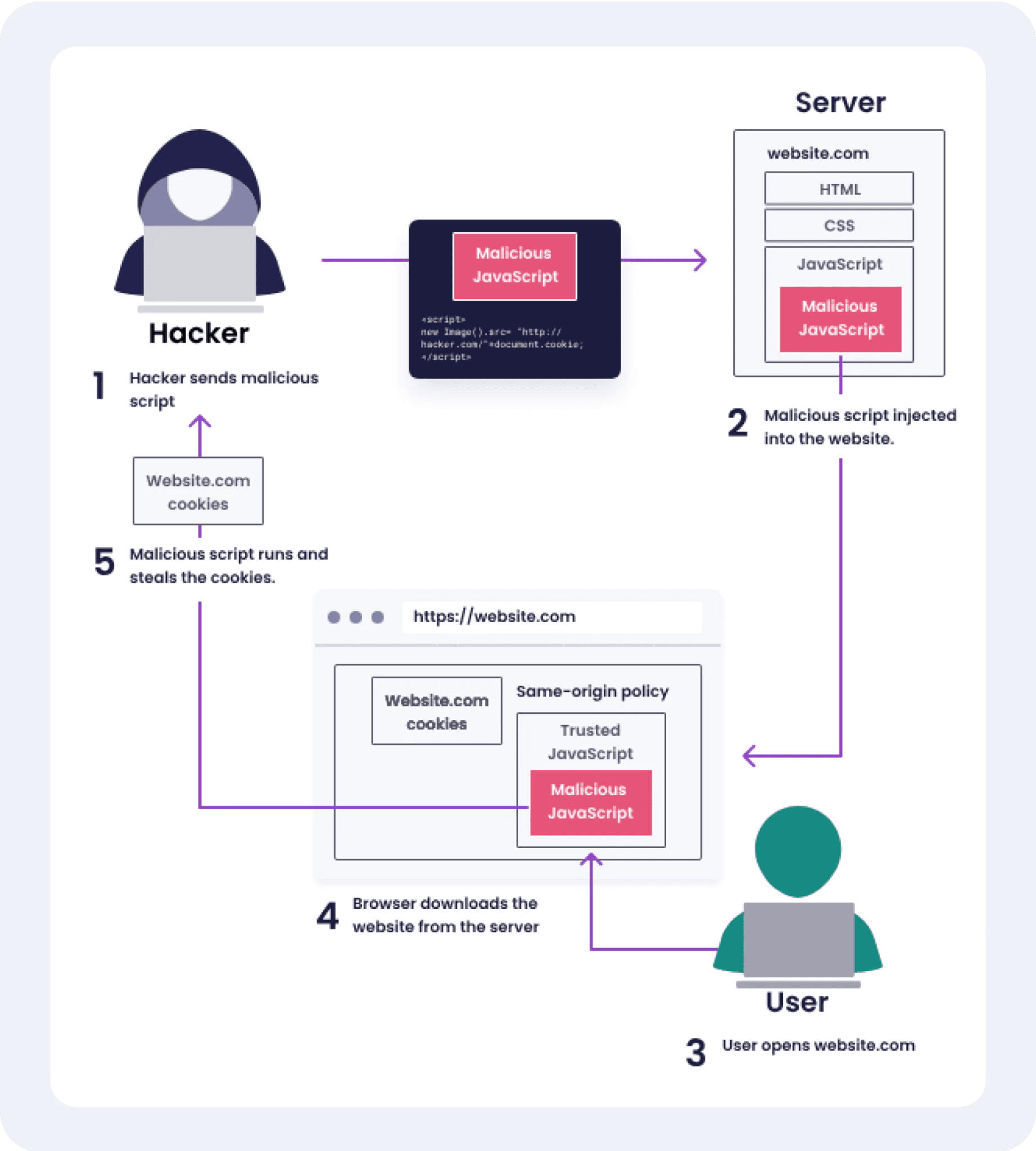
Attackers can steal session cookies, hijack user accounts, or redirect users to malicious sites. The server's reputation suffers if users experience compromised security while interacting with its services.
Remote Code Execution (RCE)
RCE vulnerabilities allow attackers to run arbitrary code on the server by exploiting poorly secured software. This is often achieved via malicious file uploads or crafted requests.
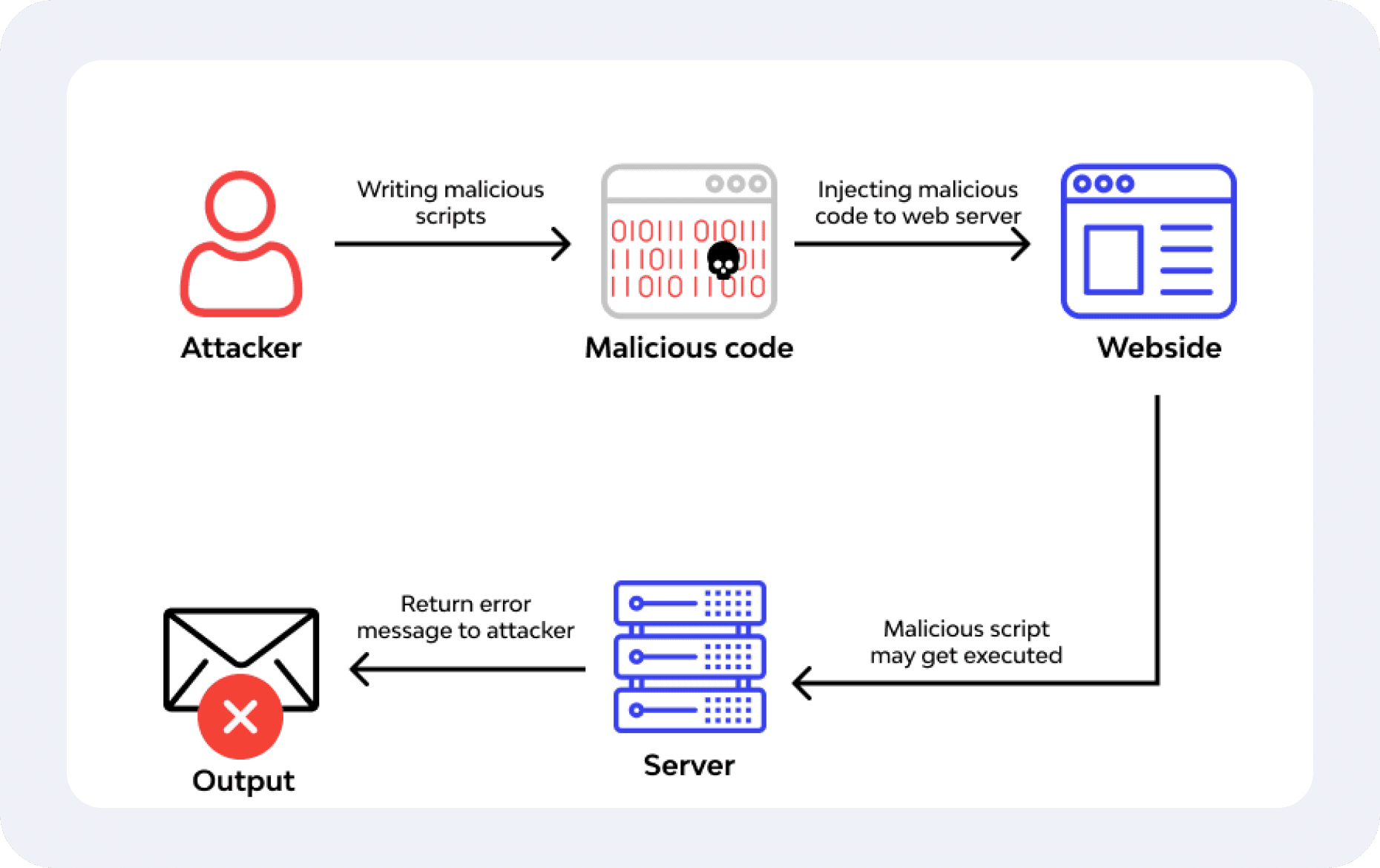
An attacker could take full control of the web server, install malware, or extract sensitive data. This can lead to widespread system disruption and data breaches.
Cross-Site Request Forgery (CSRF)
A CSRF attack tricks an authenticated user into executing unwanted actions on a web application without their consent, such as transferring money or changing account settings.
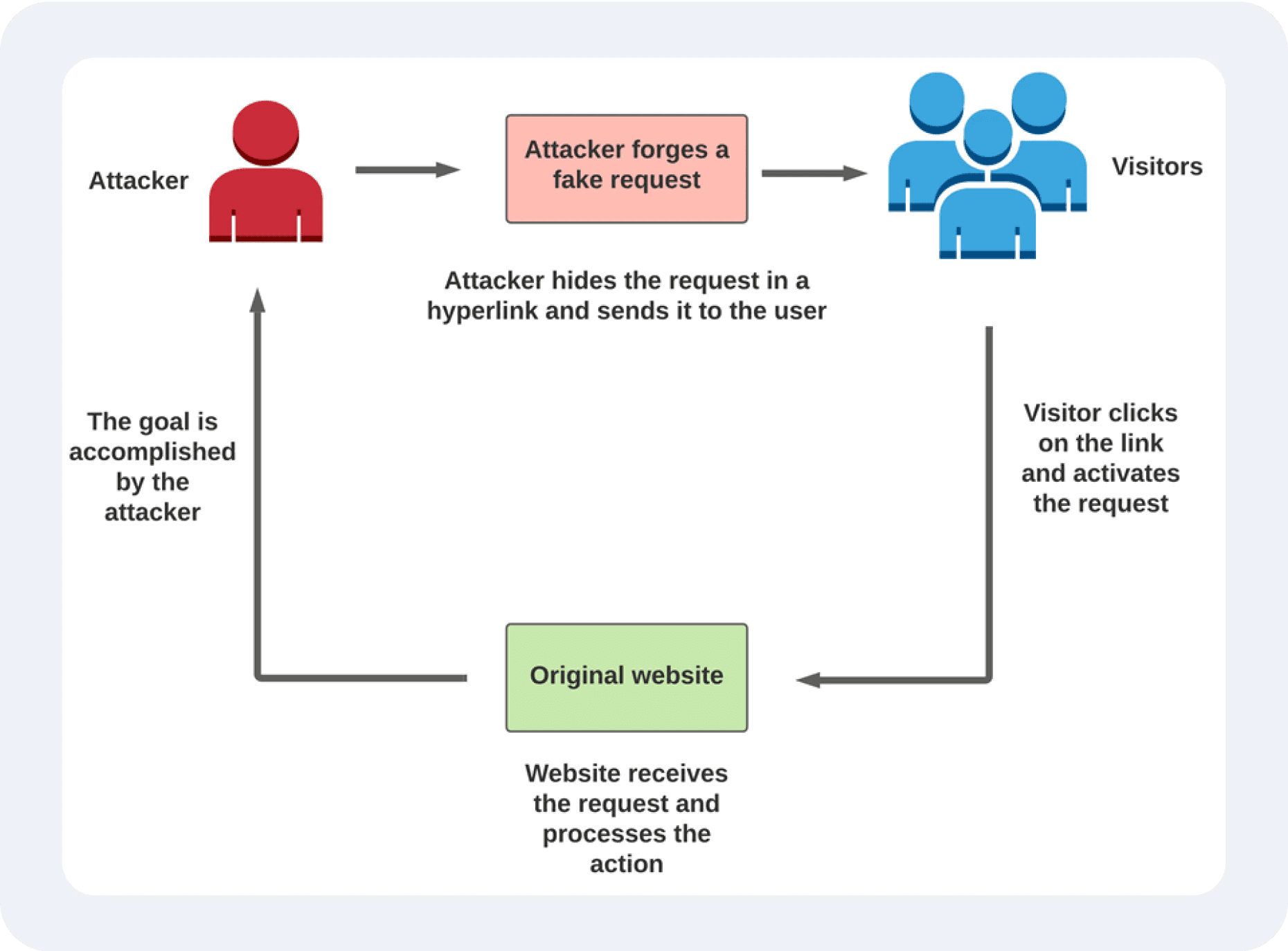
These attacks can result in unauthorised transactions, stolen funds, or unauthorised changes to user accounts, eroding trust in the application.
Brute-Force and Credential Stuffing Attacks
Attackers repeatedly try different username-password combinations to gain access or use leaked credentials from other breaches to exploit weak passwords.
Unauthorised access can lead to stolen data, misuse of web server resources, or further exploitation of the compromised account for phishing or other attacks.
Unpatched Vulnerabilities
Outdated web server software or plugins often contain known vulnerabilities that attackers can exploit if patches are not applied promptly.
Attackers can exploit these vulnerabilities to gain unauthorised access, inject malware, or disrupt services. The longer a vulnerability remains unpatched, the greater the risk of exploitation.
Man-in-the-Middle (MITM) Attacks
Attackers intercept and manipulate communication between a user and the server, often due to a lack of encryption or poorly configured SSL/TLS settings.
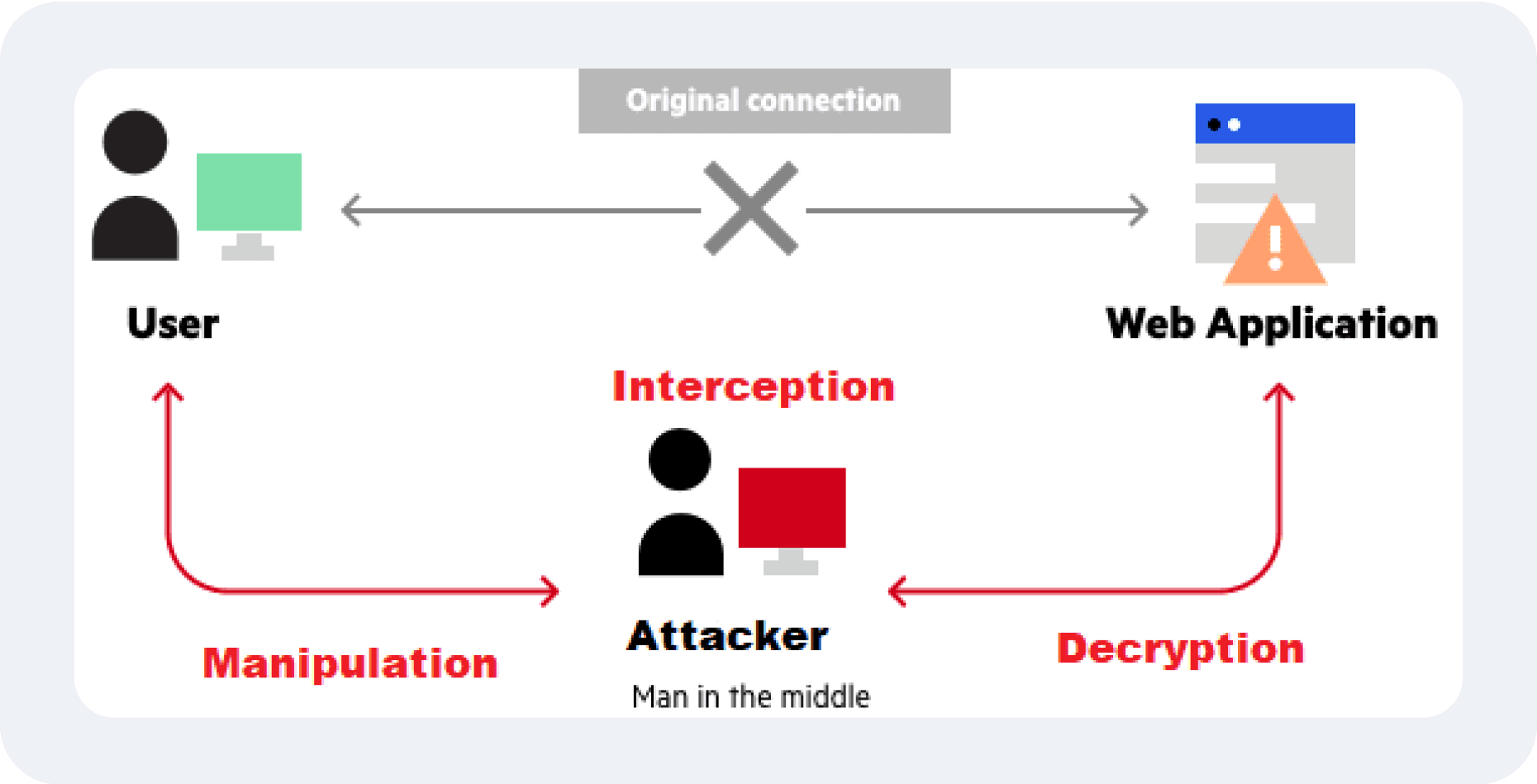
Sensitive information, such as login credentials or payment details, can be stolen, leading to identity theft and fraud.
Insider Threats
Employees, contractors, or partners with legitimate access may intentionally or accidentally misuse their privileges, compromising server security.
Insider actions can lead to data theft, sabotage, or compliance violations, making it difficult to pinpoint and address the source of the threat.
File Inclusion Vulnerabilities
Attackers exploit weaknesses in file inclusion mechanisms (e.g., PHP scripts) to include unauthorised or malicious files in server operations.
This can result in unauthorised code execution, malware deployment, or full web server compromise.
Misconfigured Server Settings
Common issues include open ports, default credentials, weak permissions, and exposed configuration files. These provide easy entry points for attackers.
Misconfigurations often lead to unauthorised access, data breaches, and exploitation of server resources for malicious purposes.
Insecure APIs
Poorly secured APIs used for communication between the server and external systems can expose sensitive data or allow unauthorised actions.
Attackers can exploit APIs to leak sensitive data, manipulate transactions, or gain access to server resources.
Zero-Day Vulnerabilities
These are newly discovered vulnerabilities for which no patch exists yet. Attackers exploit these before developers can issue a fix.
Zero-day exploits can lead to full system compromise, data breaches, or widespread attacks that are hard to defend against initially.
Physical Security Risks
On-premises servers may be physically accessed by unauthorised individuals, resulting in theft, tampering, or damage to hardware.
Physical breaches can lead to the loss of sensitive data or critical hardware, disrupting operations and causing financial losses.
Social Engineering and Phishing
Attackers manipulate users or administrators into revealing sensitive information, such as passwords or web server access details.
This can lead to unauthorised access, server manipulation, or further attacks targeting the organisation or its clients.
Poor Logging and Monitoring
Without proper logs or real-time monitoring, detecting suspicious activity or understanding the scope of a security incident becomes difficult.
Delayed detection can allow attackers to remain in the system longer, causing more extensive damage.
Data Exposure via Misconfigured Storage
Open cloud storage buckets or unencrypted databases can expose sensitive data to unauthorised users.
Data breaches can result in compliance violations, reputational harm, and loss of customer trust.
SSL/TLS Vulnerabilities
Outdated encryption protocols (e.g., SSL or older versions of TLS) or improper certificate configurations can leave communications vulnerable to decryption.
Data interception and identity theft can occur, compromising user trust and privacy.
Supply Chain Attacks
Attackers compromise third-party software components, libraries, or plugins the server uses to inject malicious code or create backdoors.
These attacks can spread malware, enable unauthorised access, and compromise server integrity on a large scale.
Best Practices for Securing Web Servers
Securing web servers is critical for maintaining the confidentiality, integrity, and availability of your web services. Below are best practices for securing web servers:
Keep the Server Software Updated
Regularly check for updates and security patches for your operating system, web server software (like Apache, NGINX, or IIS), and any applications running on the server. Outdated software often contains vulnerabilities that hackers can exploit.
Subscribe to vendor mailing lists or security bulletins for timely alerts about new vulnerabilities or patches. Automate updates where feasible, but always test them in a staging environment before applying them to production web servers.
Configure Secure Access Controls
Set strong, unique passwords for all administrative accounts to prevent unauthorised access. Implement the principle of least privilege by ensuring that users and applications only have the permissions necessary to perform their tasks. Avoid using high-privilege accounts (like root or administrator) for everyday operations. Enable Multi-Factor Authentication (MFA) to add an extra layer of security. Limit login attempts to protect against brute-force attacks and monitor login attempts for suspicious activity.
Secure Communications
All communication between clients and the web server should be encrypted using HTTPS. Obtain and install a TLS/SSL certificate from a trusted Certificate Authority (CA).
Periodically renew the certificate to maintain its validity. Disable outdated and insecure protocols like SSL 2.0/3.0 and TLS 1.0/1.1, and enforce the use of strong encryption cyphers. Encrypt all sensitive data in transit to protect it from interception.
Harden the Web Server Configuration
Reduce your server’s attack surface by disabling features, modules, or services that are not required. For example, if your application doesn’t use WebDAV or CGI scripts, disable them. Hide server details, such as software versions, in HTTP headers to prevent attackers from gathering information about your system.
Properly configure file and directory permissions to prevent unauthorised users from modifying or accessing sensitive files. Implement Content Security Policies (CSP) and secure HTTP headers like Strict-Transport-Security, X-Content-Type-Options, and X-Frame-Options to guard against common attacks like cross-site scripting (XSS) and clickjacking.
Use a Web Application Firewall (WAF)
A Web Application Firewall (WAF) acts as a shield between your server and incoming traffic. It inspects and filters HTTP requests, blocking malicious requests such as SQL injection, cross-site scripting, and distributed denial-of-service (DDoS) attacks.
Use a managed WAF service, which gets frequent updates to counter the latest threats. Deploy a WAF to protect your web applications, even if your application code is secure.
Monitor and Log Activity
Enable logging for all server activities, including access logs, error logs, and system events. Use centralised logging tools like the ELK Stack (Elasticsearch, Logstash, and Kibana) or Splunk for easier log management and analysis.
Regularly review logs for unusual patterns, such as repeated failed login attempts or spikes in traffic, which could indicate an attack. Implement alerts to notify administrators of suspicious activity.
Implement Network Security Measures
Deploy a firewall to filter incoming and outgoing network traffic based on a set of security rules. Only allow access to the ports and services necessary for your web application to function. Use IP whitelisting to restrict access to trusted users and block known malicious IP addresses.
Consider setting up an Intrusion Detection and Prevention System (IDPS) to monitor and respond to network threats. Place your public-facing servers in a Demilitarised zone (DMZ) to isolate them from your internal network.
Regular Backups
Perform regular web server backups, including web application files, databases, and configuration files. Store backups in a secure location, such as an offsite server or encrypted storage. Regularly test your backup and restoration process to ensure you can recover data quickly in case of data loss or a security breach.
Scan for Vulnerabilities
Regularly scan your web server for vulnerabilities using tools like OpenVAS, Nessus, or Qualys. These tools can identify outdated software, misconfigurations, and potential security issues. Follow up by addressing the issues promptly, starting with the most critical vulnerabilities. Conduct periodic penetration web server security tests to simulate real-world attacks and validate the security of your system.
Protect Against Malware
Install server-level antivirus and anti-malware software to detect and remove malicious files or programs. Schedule regular scans and update the software with the latest virus definitions. If malware is detected, isolate the affected system to prevent further infection and thoroughly investigate the source.
Disable Unnecessary Services
Review the services and ports running on your server and disable any that are not actively in use. Unnecessary services can become potential entry points for attackers.
For instance, turn them off if you don’t need FTP or Telnet. Run only the applications and processes essential for your web service to minimise the server’s attack surface.
Protect Against DDoS Attacks
DDoS attacks overwhelm your web server security with traffic, making it unavailable to legitimate users. Use DDoS mitigation services like Cloudflare or AWS Shield to handle large traffic volumes.
Configure rate limiting and bandwidth throttling to prevent sudden traffic spikes from affecting server performance. Load balancers can distribute incoming traffic across multiple servers, reducing the impact of an attack.
Educate and Train Staff
Regularly train your staff on recognising and preventing phishing and social engineering attacks. Educate developers on secure coding practices, focusing on addressing the vulnerabilities highlighted in the OWASP Top 10, such as SQL injection and cross-site scripting. Awareness and training can significantly reduce the likelihood of human error compromising security.
Plan for Incident Response
Prepare an incident response plan to handle potential security breaches efficiently. The plan should include steps for identifying, containing, and mitigating the incident and procedures for notifying stakeholders.
Conduct regular drills to ensure the team is familiar with the process. Keep a list of emergency contacts, including your hosting provider and security teams, up to date.
Use Strong Authentication for APIs
Secure your API endpoints by requiring strong authentication methods, such as OAuth tokens or API keys. Regularly rotate these keys to reduce the risk of unauthorised access.
Implement rate limiting to prevent abuse of APIs and validate all input to protect against injection attacks. Properly document your APIs, including security measures, to ensure they are used securely.
Final Thoughts
Web server security is an ongoing process that requires a proactive approach to stay ahead of evolving threats. By implementing robust security measures — such as keeping software updated, configuring access controls, encrypting communications, and employing firewalls — you can significantly reduce vulnerabilities and protect your server from unauthorised access and cyberattacks.
For trading companies, where sensitive financial data and operations are at stake, maintaining web server security is not just a technical necessity but a business imperative. A secure server safeguards customer trust, ensures regulatory compliance, and provides the foundation for uninterrupted business operations.
FAQ
Why is web server security critical for a trading company?
Web server security is vital because trading companies handle sensitive data, such as financial transactions and customer information.
What role does encryption play in web server security?
Encryption protects sensitive data in transit (via HTTPS and TLS certificates) and at rest (using standards like AES-256).
What is a web application firewall, and why is it important?
A WAF filters and monitors HTTP/HTTPS traffic to protect against common web application attacks like SQL injection and cross-site scripting (XSS).
Why is backup and disaster recovery essential for trading companies?
Regular backups ensure that critical data can be restored in case of hardware failure, ransomware attacks, or natural disasters. A disaster recovery plan minimises downtime, guaranteeing continuity of trading operations even during crises.
Read also





